Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags
Related Articles: Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags
- 2 Introduction
- 3 Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags
- 3.1 Understanding Nmap Flags: The Keys to Network Discovery
- 3.2 Essential Nmap Flags: A Foundation for Exploration
- 3.3 Nmap Flags for Targeted Information Gathering
- 3.4 Advanced Nmap Flags: Tailoring Scans for Specific Needs
- 3.5 Frequently Asked Questions (FAQs) about Nmap Flags
- 3.6 Tips for Utilizing Nmap Flags Effectively
- 3.7 Conclusion: Empowering Network Exploration with Nmap Flags
- 4 Closure
Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags

Nmap, the Network Mapper, is a powerful and versatile tool for network exploration and security auditing. Its flexibility lies in its extensive command-line options, known as flags, which allow users to tailor scans to specific needs. This guide provides a comprehensive overview of Nmap flags, their functionalities, and practical applications.
Understanding Nmap Flags: The Keys to Network Discovery
Nmap flags are essential for directing the tool’s behavior and customizing scan parameters. They dictate the type of scan, target selection, port range, timing, output format, and various other aspects. Understanding these flags empowers users to conduct targeted scans, gather specific information, and ultimately gain deeper insights into network infrastructure.
Essential Nmap Flags: A Foundation for Exploration
-sT (TCP SYN Scan): This flag initiates a SYN scan, sending a TCP SYN packet to each target port. The scan identifies open ports by analyzing the response received from the target. It is a stealthy scan as it does not complete the TCP handshake, making it less likely to trigger intrusion detection systems (IDS).
-sS (TCP SYN Stealth Scan): This flag performs a stealth SYN scan, similar to -sT, but it uses the TCP SYN packet to determine the port state. This technique is more stealthy as it avoids establishing a full TCP connection, reducing the chances of detection by firewalls or intrusion prevention systems (IPS).
-sU (UDP Scan): This flag conducts a UDP scan, sending UDP packets to each target port. It determines the port state based on the response received. While UDP scans are less stealthy than TCP scans, they are essential for identifying UDP-based services.
-sC (Connect Scan): This flag initiates a connect scan, establishing a full TCP connection to each target port. While not as stealthy as SYN scans, it provides more accurate results and is useful for identifying services that might not respond to SYN packets.
-sN (Null Scan): This flag performs a null scan, sending a TCP packet with all flags set to zero. It is useful for identifying open ports that are not responsive to other types of scans.
-sF (FIN Scan): This flag conducts a FIN scan, sending a TCP packet with the FIN flag set. It is considered a stealthy scan as it does not complete the TCP handshake.
-sX (Xmas Scan): This flag initiates an Xmas scan, sending a TCP packet with the FIN, PSH, and URG flags set. It is a stealthy scan that can identify open ports that are not responsive to other types of scans.
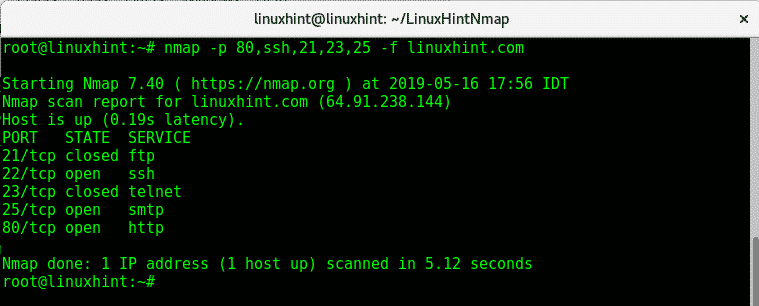
-p (Port Specification): This flag allows users to specify the target port range for the scan. It can be used to scan specific ports, a range of ports, or all ports. For example, "-p 80,443" scans ports 80 and 443, while "-p 1-1024" scans all ports from 1 to 1024.
-T (Timing Template): This flag defines the scan speed, influencing the rate at which Nmap sends packets to the target. It offers various timing templates, ranging from "S" (slow) to "0" (fastest). Choosing the appropriate timing template helps balance scan speed with stealthiness.
-O (Operating System Detection): This flag enables Nmap to attempt operating system detection based on the target’s responses to probes. It uses a database of known operating system fingerprints to identify the target’s operating system.
-v (Verbose Output): This flag increases the verbosity of the output, providing more detailed information about the scan results.
-A (Aggressive Scan): This flag performs a more aggressive scan, including various scripts and probes to gather more detailed information about the target.
-Pn (No Ping Scan): This flag disables the initial ping scan, which is used to identify active hosts. This is useful when scanning behind firewalls or in situations where ping responses are blocked.
-D (Decoy Scan): This flag allows users to specify decoy IP addresses to confuse target systems and make it harder to identify the source of the scan.
-f (Fragmentation Scan): This flag fragments the scan packets to bypass firewalls or intrusion detection systems that might be blocking non-fragmented traffic.
-g (Gateway Scan): This flag specifies a gateway IP address to use for the scan. This is useful when scanning through a proxy or NAT device.
Nmap Flags for Targeted Information Gathering
-sV (Service Version Detection): This flag attempts to identify the version of the service running on each open port. This information is invaluable for assessing vulnerabilities and understanding the target’s security posture.
-script (Script Scanning): This flag allows users to run Nmap scripts against the target. These scripts perform various tasks, such as identifying vulnerabilities, checking for open ports, and gathering information about the target’s services.
-oN (Normal Output): This flag saves the scan results to a plain text file.
-oX (XML Output): This flag saves the scan results in XML format, which is suitable for further processing and analysis.
-oG (Grepable Output): This flag saves the scan results in a format suitable for grep-like text processing tools.
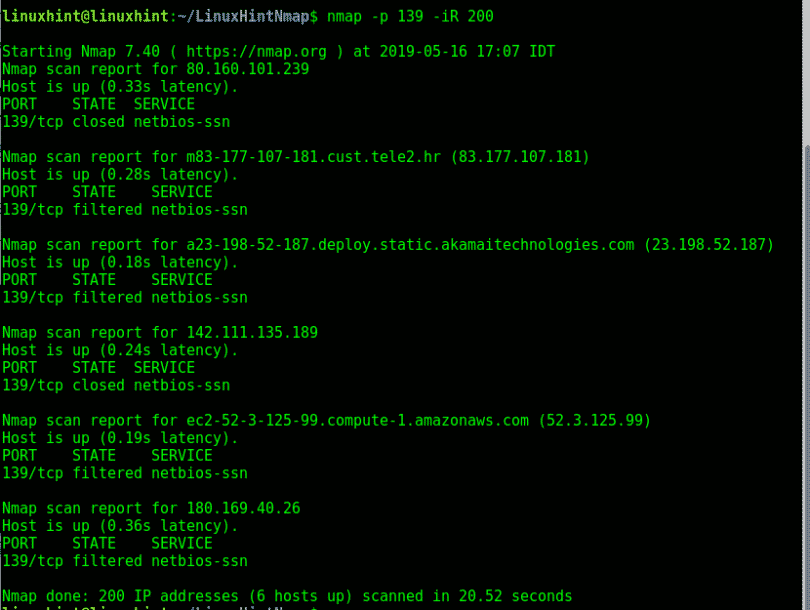
-iL (Input File): This flag specifies a file containing a list of target IP addresses or hostnames.
-T4 (Timing Template 4): This flag uses a timing template that balances scan speed with stealthiness, suitable for general network exploration.
-F (Fast Scan): This flag performs a fast scan, limiting the scan to the most common ports.
-r (Randomize Port Order): This flag randomizes the order in which ports are scanned, making the scan more difficult to detect and analyze.
-n (No DNS Resolution): This flag disables DNS resolution, preventing Nmap from resolving hostnames to IP addresses.
-b (Banner Grabbing): This flag enables banner grabbing, which retrieves service banners from open ports.
Advanced Nmap Flags: Tailoring Scans for Specific Needs
-sS (SYN Stealth Scan): This flag performs a stealth SYN scan, which is less likely to trigger intrusion detection systems.
-sW (Window Scan): This flag performs a window scan, which is a stealthy scan that uses the TCP window size to determine the port state.
-sM (Maimon Scan): This flag performs a Maimon scan, which is a stealthy scan that uses the TCP maximum segment size (MSS) to determine the port state.
-sI (Idle Scan): This flag performs an idle scan, which is a stealthy scan that uses a zombie host to probe the target.
-sY (FTP Bounce Scan): This flag performs an FTP bounce scan, which uses an FTP server to bounce packets to the target.
-p (Port Specification): This flag allows users to specify a custom port range to scan.
-O (Operating System Detection): This flag enables Nmap to attempt operating system detection based on the target’s responses to probes.
-A (Aggressive Scan): This flag performs a more aggressive scan, including various scripts and probes to gather more detailed information about the target.
-D (Decoy Scan): This flag allows users to specify decoy IP addresses to confuse target systems and make it harder to identify the source of the scan.
-f (Fragmentation Scan): This flag fragments the scan packets to bypass firewalls or intrusion detection systems that might be blocking non-fragmented traffic.
-g (Gateway Scan): This flag specifies a gateway IP address to use for the scan. This is useful when scanning through a proxy or NAT device.
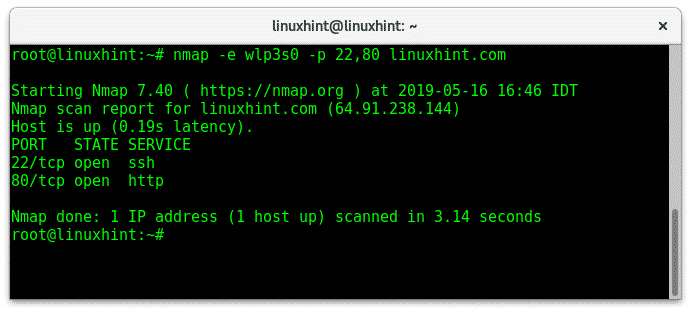
-e (Interface Selection): This flag specifies the network interface to use for the scan.
-d (Defer Scan): This flag defers the scan to a later time.
-M (Max Parallelism): This flag specifies the maximum number of parallel scans to perform.
-T (Timing Template): This flag defines the scan speed, influencing the rate at which Nmap sends packets to the target.
-c (Number of Probes): This flag specifies the number of probes to send per port.
-w (Timeout): This flag specifies the timeout for each probe.
-r (Randomize Port Order): This flag randomizes the order in which ports are scanned, making the scan more difficult to detect and analyze.
-n (No DNS Resolution): This flag disables DNS resolution, preventing Nmap from resolving hostnames to IP addresses.
-b (Banner Grabbing): This flag enables banner grabbing, which retrieves service banners from open ports.
-sL (List Scan): This flag performs a list scan, which simply lists the target IP addresses without performing any actual scanning.
-sR (RPC Scan): This flag performs an RPC scan, which identifies and enumerates RPC services on the target.
-sV (Service Version Detection): This flag attempts to identify the version of the service running on each open port.
-script (Script Scanning): This flag allows users to run Nmap scripts against the target. These scripts perform various tasks, such as identifying vulnerabilities, checking for open ports, and gathering information about the target’s services.
-oN (Normal Output): This flag saves the scan results to a plain text file.
-oX (XML Output): This flag saves the scan results in XML format, which is suitable for further processing and analysis.
-oG (Grepable Output): This flag saves the scan results in a format suitable for grep-like text processing tools.
-iL (Input File): This flag specifies a file containing a list of target IP addresses or hostnames.
-oA (All Output): This flag saves the scan results in all supported output formats.
-v (Verbose Output): This flag increases the verbosity of the output, providing more detailed information about the scan results.
-d (Debug Output): This flag enables debug output, providing more detailed information about the scan process.
Frequently Asked Questions (FAQs) about Nmap Flags
1. What is the difference between a SYN scan and a Connect scan?
A SYN scan (using the -sS flag) only sends a SYN packet to the target port, not completing the TCP handshake. This makes it stealthier than a Connect scan (using the -sC flag), which establishes a full TCP connection. While SYN scans are faster and less likely to trigger security systems, Connect scans provide more accurate results as they fully establish a connection.
2. How do I scan a specific port range?
Use the -p flag followed by the desired port range. For example, -p 80,443 scans ports 80 and 443, while -p 1-1024 scans all ports from 1 to 1024.
3. What is the purpose of the -T flag?
The -T flag sets the scan timing template, controlling the rate at which Nmap sends packets. Different templates offer varying scan speeds, allowing users to balance scan speed with stealthiness. For instance, -T4 provides a balanced approach, while -T0 is the fastest but less stealthy.
4. How do I run Nmap scripts?
Use the -script flag followed by the name of the script. For example, -script http-title runs the http-title script, which retrieves the HTTP title of web servers.
5. How can I save the scan results in different formats?
Nmap offers various output formats for saving scan results. Use -oN for plain text, -oX for XML, -oG for grepable output, and -oA for all formats.
Tips for Utilizing Nmap Flags Effectively
-
Start with basic scans: Begin with simple scans like SYN scans (
-sS) or Connect scans (-sC) to identify open ports and services. - Use scripts for targeted information: Employ Nmap scripts to gather specific information about the target, such as vulnerabilities, service versions, or operating system details.
-
Customize scan speed: Adjust the scan timing template (
-T) based on your needs. For stealthy scans, use slower templates like-T4, while for faster scans, use-T0. - Experiment with different flags: Explore various flags to tailor scans to your specific requirements.
-
Document your findings: Save scan results in appropriate formats (
-oN,-oX,-oG) for future reference and analysis.
Conclusion: Empowering Network Exploration with Nmap Flags
Nmap flags are the foundation of network exploration and security auditing. Understanding and utilizing these flags empowers users to conduct targeted scans, gather specific information, and gain deeper insights into network infrastructure. By leveraging the flexibility of Nmap’s command-line options, users can effectively explore networks, identify vulnerabilities, and enhance their security posture. The comprehensive guide provided here serves as a stepping stone for mastering Nmap’s capabilities and unlocking the full potential of network exploration.



Closure
Thus, we hope this article has provided valuable insights into Mastering the Art of Network Exploration: A Comprehensive Guide to Nmap Flags. We thank you for taking the time to read this article. See you in our next article!
