Navigating Memory with mmap Flags: A Comprehensive Guide
Related Articles: Navigating Memory with mmap Flags: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating Memory with mmap Flags: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating Memory with mmap Flags: A Comprehensive Guide
- 2 Introduction
- 3 Navigating Memory with mmap Flags: A Comprehensive Guide
- 3.1 Understanding the Core: Memory Mapping Flags
- 3.2 The Importance of Memory Mapping Flags
- 3.3 Practical Applications of Memory Mapping Flags
- 3.4 Common FAQs Regarding Memory Mapping Flags
- 3.5 Tips for Efficient Memory Mapping
- 3.6 Conclusion: Mastering Memory Mapping Flags
- 4 Closure
Navigating Memory with mmap Flags: A Comprehensive Guide
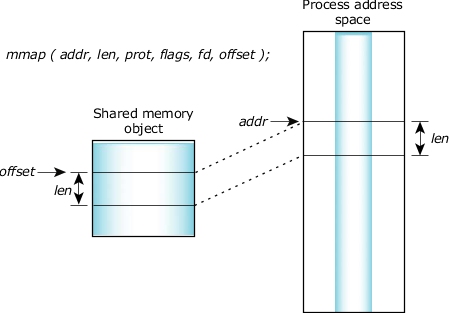
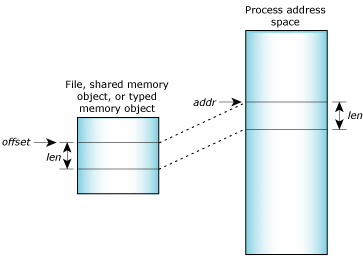
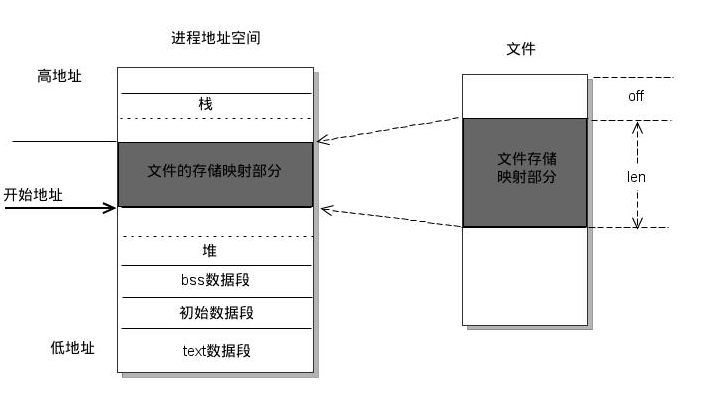
The mmap() system call is a powerful tool in the Unix-like operating systems, enabling programs to access files and other memory-mapped resources directly within their address space. This direct access significantly enhances performance by eliminating the overhead associated with traditional file I/O operations. However, the efficiency and behavior of mmap() depend heavily on the flags specified during the mapping process. These flags, known as memory mapping flags, act as control parameters, dictating how the operating system manages the mapped memory region.
This article delves into the intricacies of memory mapping flags, providing a comprehensive understanding of their functionality and implications for program behavior. By exploring the various flags and their combinations, we aim to equip developers with the knowledge to optimize memory usage and achieve desired performance characteristics.
Understanding the Core: Memory Mapping Flags
Memory mapping flags, passed as arguments to the mmap() system call, control the behavior of the mapped memory region. These flags determine aspects such as:
- Read/Write Access: Whether the mapped memory can be read from, written to, or both.
- File Sharing: How multiple processes can share access to the mapped file.
- Memory Allocation: How the operating system allocates physical memory for the mapped region.
- Data Synchronization: Whether modifications to the mapped region are automatically reflected in the underlying file.
The most commonly used flags are:
1. Access Modes:
-
PROT_READ: Grants read access to the mapped memory region. -
PROT_WRITE: Grants write access to the mapped memory region. -
PROT_EXEC: Grants execute access to the mapped memory region. This flag is typically used for mapping executable code segments. -
PROT_NONE: Denies all access to the mapped memory region. This flag is often used to temporarily disable access to a specific memory region for security or debugging purposes.
2. Sharing Modes:
-
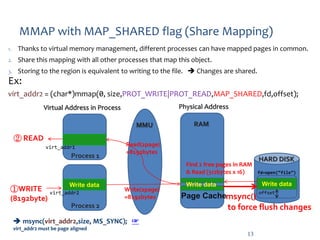
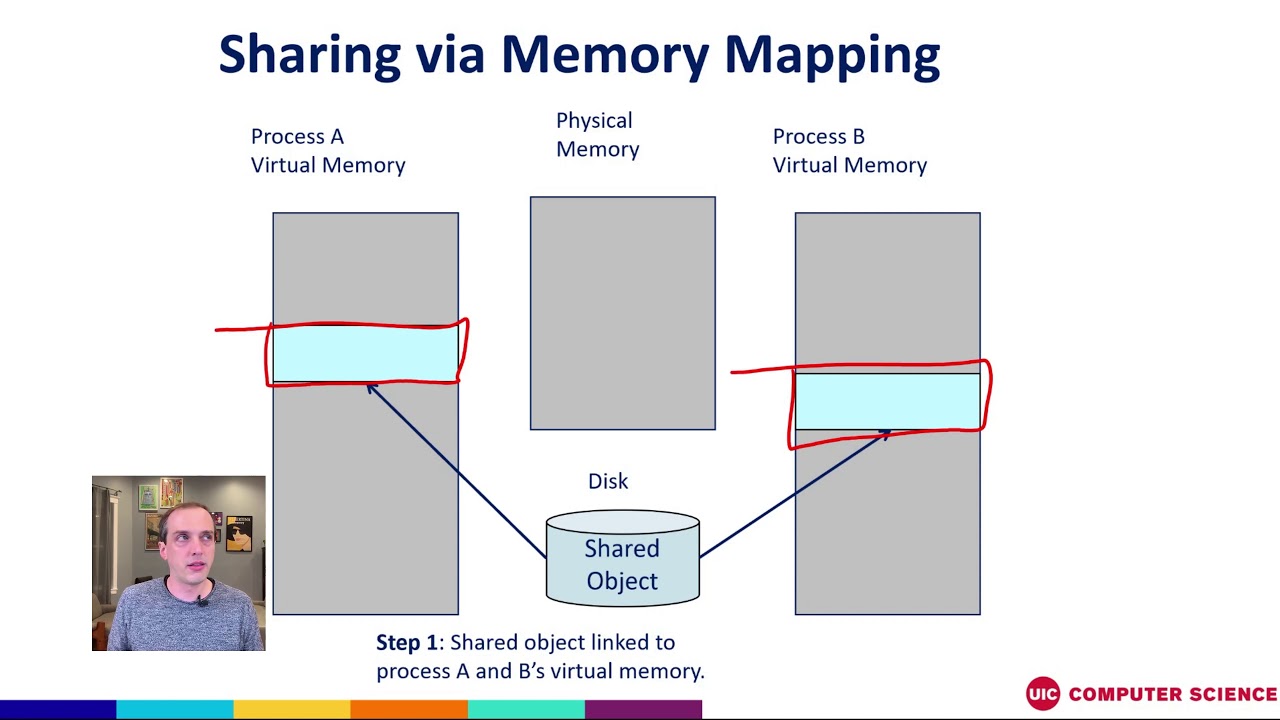
MAP_SHARED: Allows multiple processes to share the same mapped memory region. Changes made by one process are visible to all other processes sharing the region. This flag is commonly used for inter-process communication and data sharing. -
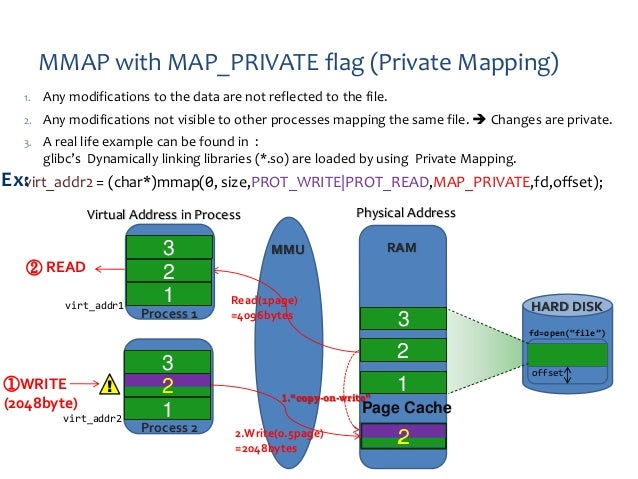
MAP_PRIVATE: Creates a private copy of the mapped memory region for each process. Changes made by one process are not visible to other processes. This flag is useful for isolating memory regions and preventing unintended side effects.
3. Memory Allocation Modes:
-
MAP_ANONYMOUS: Creates an anonymous mapping, which is not backed by any file. This allows for allocation of memory without needing a backing file. This flag is often used for dynamic memory allocation and shared memory segments. -
MAP_FIXED: Attempts to fix the mapped memory region at the specified address. This flag can be useful for specific memory layout requirements but should be used with caution as it may lead to memory conflicts or address space fragmentation. -
MAP_LOCKED: Locks the mapped memory region in physical memory, preventing it from being swapped out to disk. This can improve performance for frequently accessed data but may lead to higher memory usage and potential memory fragmentation.
4. Data Synchronization Modes:
-
MAP_SYNC: Ensures that writes to the mapped memory region are synchronized with the underlying file. This flag is typically used for applications where data consistency is critical, such as databases or file systems. -
MAP_ASYNC: Allows for asynchronous writes to the mapped memory region. This can improve performance by allowing the operating system to write data to the file in the background. However, it may lead to data inconsistencies if the application crashes before the writes are completed.
5. Other Flags:
-
MAP_POPULATE: Pre-populates the mapped memory region with data from the underlying file. This can improve performance for applications that require immediate access to the file data. -
MAP_DENYWRITE: Prevents other processes from writing to the mapped file, even if they haveMAP_SHAREDaccess. -
MAP_HUGETLB: Requests the use of huge pages for the mapped memory region. This can improve performance for large memory allocations by reducing the number of page table entries required.
The Importance of Memory Mapping Flags
The proper selection of memory mapping flags is crucial for optimizing program performance and ensuring data integrity. By understanding the implications of each flag, developers can:
-
Enhance Performance: Utilize
MAP_LOCKEDto improve performance for frequently accessed data. EmployMAP_HUGETLBfor large memory allocations. LeverageMAP_POPULATEto pre-populate memory for immediate access. -
Ensure Data Consistency: Utilize
MAP_SYNCto guarantee data consistency between the mapped memory region and the underlying file, crucial for applications requiring data integrity. -
Facilitate Inter-Process Communication: Employ
MAP_SHAREDfor efficient inter-process communication and data sharing. -
Optimize Memory Usage: Choose
MAP_PRIVATEto create private copies of the mapped memory region, preventing unintended side effects. UseMAP_ANONYMOUSfor dynamic memory allocation without needing a backing file. -
Manage Memory Access: Utilize
PROT_READ,PROT_WRITE, andPROT_EXECto grant or restrict access to specific memory regions based on program requirements.
Practical Applications of Memory Mapping Flags
Memory mapping flags find extensive applications in various domains, including:
- File System Implementations: File systems extensively utilize memory mapping to efficiently manage file data in memory.
- Database Systems: Databases employ memory mapping for storing and accessing large datasets, ensuring data integrity and performance.
- Web Servers: Web servers use memory mapping to cache frequently accessed web content, reducing server load and improving response times.
- Graphics Processing: Graphics applications leverage memory mapping to access and manipulate large graphics data structures, enabling efficient rendering and image processing.
- Scientific Computing: Scientific simulations and data analysis often involve manipulating massive datasets. Memory mapping provides a powerful tool for handling these large data structures efficiently.
Common FAQs Regarding Memory Mapping Flags
1. What is the difference between MAP_SHARED and MAP_PRIVATE?
MAP_SHARED allows multiple processes to share the same mapped memory region, with changes made by one process visible to all others. MAP_PRIVATE creates a private copy of the mapped region for each process, isolating changes made by one process from others.
2. When should I use MAP_LOCKED?
MAP_LOCKED is beneficial for frequently accessed data, preventing it from being swapped out to disk. However, it can lead to higher memory usage and potential fragmentation. Consider using it carefully, especially for large datasets.
3. Can I use multiple flags simultaneously?
Yes, you can combine multiple flags to achieve specific behavior. For example, you can use PROT_READ and PROT_WRITE to allow both read and write access to the mapped region.
4. What happens if I don’t specify any flags?
If you don’t specify any flags, the mmap() system call will use default values, which may not be optimal for your application. It’s crucial to understand the default behavior and select appropriate flags for your specific needs.
5. How do I choose the appropriate flags for my application?
The choice of flags depends on your application’s requirements. Consider factors such as data sharing, access modes, memory allocation, and data synchronization. Carefully analyze your application’s behavior and select flags that optimize performance and ensure data integrity.
Tips for Efficient Memory Mapping
-
Avoid
MAP_FIXED: While it can be tempting to useMAP_FIXEDfor precise memory layout, it can lead to memory conflicts and fragmentation. Consider usingMAP_ANONYMOUSwithmmap()to dynamically allocate memory. -
Optimize for Data Access: Use
MAP_LOCKEDfor frequently accessed data, but be mindful of memory usage and fragmentation. -
Utilize
MAP_POPULATE: Pre-populate memory with data from the underlying file for immediate access, improving performance for applications requiring quick data retrieval. -
Choose the Right Sharing Mode:
MAP_SHAREDis ideal for inter-process communication and data sharing, whileMAP_PRIVATEis suitable for isolating memory regions and preventing unintended side effects. -
Ensure Data Consistency: Use
MAP_SYNCto guarantee data consistency between the mapped memory region and the underlying file, particularly important for applications requiring data integrity.
Conclusion: Mastering Memory Mapping Flags
Memory mapping flags are essential for achieving optimal performance and data integrity in Unix-like operating systems. By understanding the implications of each flag, developers can tailor memory mapping behavior to meet specific program requirements. Careful selection of flags enables efficient memory usage, facilitates inter-process communication, and ensures data consistency, ultimately leading to robust and high-performing applications.



Closure
Thus, we hope this article has provided valuable insights into Navigating Memory with mmap Flags: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!