Nmap: A Powerful Tool for Network Exploration and Security Auditing
Related Articles: Nmap: A Powerful Tool for Network Exploration and Security Auditing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap: A Powerful Tool for Network Exploration and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Nmap: A Powerful Tool for Network Exploration and Security Auditing
- 2 Introduction
- 3 Nmap: A Powerful Tool for Network Exploration and Security Auditing
- 3.1 Understanding Nmap’s Functionality
- 3.2 Ethical Applications of Nmap
- 3.3 Ethical Considerations and Best Practices
- 3.4 FAQs on Nmap Ethical Hacking
- 3.5 Tips for Using Nmap Effectively
- 3.6 Conclusion
- 4 Closure
Nmap: A Powerful Tool for Network Exploration and Security Auditing
Nmap, or Network Mapper, is a versatile and powerful open-source tool widely used for network exploration, security auditing, and vulnerability assessment. Developed by Gordon Lyon, also known as Fyodor, Nmap has become an indispensable resource for network administrators, security professionals, and ethical hackers worldwide. This article aims to provide a comprehensive overview of Nmap, exploring its capabilities, applications, and ethical considerations.
Understanding Nmap’s Functionality
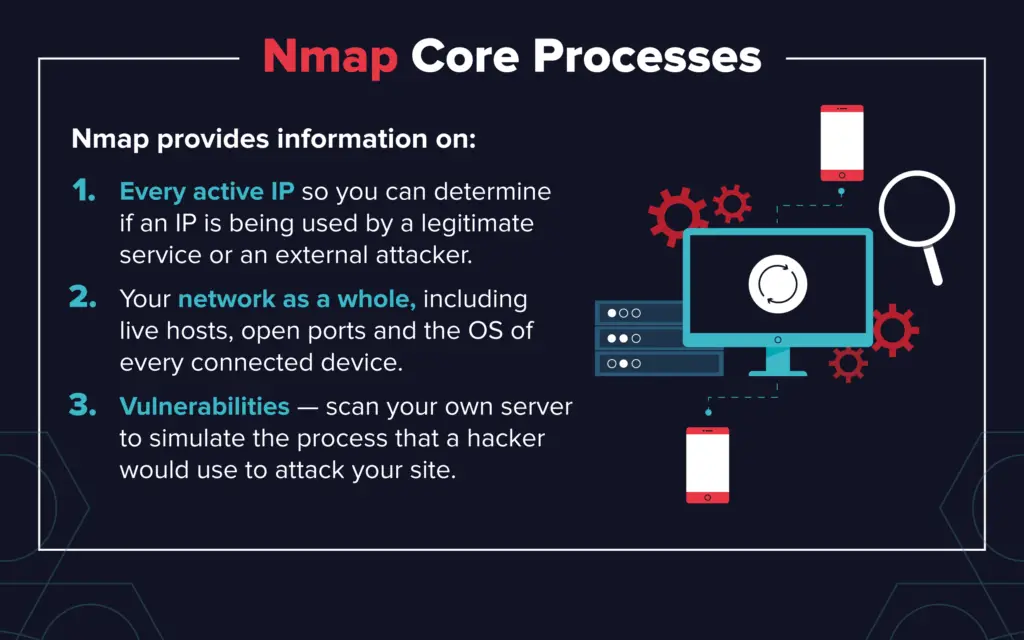
Nmap operates by sending specially crafted packets to target networks and analyzing the responses. This process, known as network scanning, allows Nmap to gather crucial information about network hosts, including:
- Host Discovery: Identifying active hosts on a network, their operating systems, and open ports.
- Port Scanning: Determining which ports are open on each host, revealing potential services running on those ports.
- Service Version Detection: Identifying the specific versions of services running on open ports, enabling vulnerability analysis.
- Operating System Detection: Identifying the operating systems of target hosts, facilitating targeted attacks or vulnerability exploitation.
- Network Mapping: Visualizing network topology, including the relationships between hosts and their connections.
Nmap’s versatility lies in its ability to customize scanning techniques, including:
- TCP/UDP Scan Types: Nmap offers various scanning methods, such as SYN scan, connect scan, and UDP scan, allowing for tailored approaches based on network security posture and desired information.
- Script Scanning: Nmap’s extensive script library enables automated vulnerability checks, service fingerprinting, and even remote exploitation of known vulnerabilities.
- Timing and Speed: Nmap provides options to adjust scan speed and timing, balancing efficiency with stealth and minimizing network impact.
- Output Formats: Nmap offers various output formats, including text, XML, and Nmap’s own NSE (Nmap Scripting Engine) format, allowing for seamless integration with other tools and data analysis platforms.
Ethical Applications of Nmap
Nmap’s capabilities extend beyond security auditing and vulnerability assessment, finding valuable applications in various legitimate scenarios:
- Network Inventory Management: Nmap helps network administrators map their networks, identify connected devices, and manage network resources efficiently.
- Troubleshooting Network Issues: Nmap assists in identifying network bottlenecks, connectivity problems, and other network issues by pinpointing network devices and their configurations.
- Network Security Monitoring: Nmap can be used to monitor network activity, detect unauthorized devices, and identify potential security threats.
- Research and Development: Nmap provides a valuable tool for network research, enabling analysis of network protocols and security vulnerabilities.
- Educational Purposes: Nmap is widely used in cybersecurity education, providing students with hands-on experience in network scanning and security analysis.
Ethical Considerations and Best Practices
While Nmap is a powerful tool with legitimate applications, it’s crucial to use it responsibly and ethically. Improper use can lead to legal consequences and ethical concerns. Here are some important considerations:
- Obtain Permission: Always obtain explicit permission from network owners before scanning their networks.
- Respect Privacy: Avoid scanning personal networks or devices without consent.
- Avoid Malicious Activities: Do not use Nmap to exploit vulnerabilities, launch attacks, or cause harm to networks or individuals.
- Follow Legal Regulations: Adhere to all applicable laws and regulations regarding network scanning and security testing.
- Use Nmap Responsibly: Exercise caution and avoid unnecessary or disruptive scans.
FAQs on Nmap Ethical Hacking
1. Is Nmap legal to use?
Nmap itself is legal to use for legitimate purposes, such as network administration, security auditing, and research. However, using it for illegal activities, such as unauthorized access or malicious attacks, can lead to legal consequences.
2. Can Nmap be used for hacking?
Yes, Nmap can be used for hacking, but this is unethical and illegal. Nmap’s capabilities can be misused to identify vulnerabilities and launch attacks.
3. How can I use Nmap ethically?
Use Nmap for legitimate purposes, such as network administration, security auditing, and research. Always obtain permission before scanning networks, respect privacy, and avoid malicious activities.
4. What are some ethical Nmap scan examples?
- Scanning your own network to identify connected devices and potential vulnerabilities.
- Scanning a network with permission to assess security posture and identify potential attack surfaces.
- Using Nmap for research purposes, such as analyzing network protocols or vulnerabilities.
5. What are the risks of using Nmap?
Using Nmap without permission can lead to legal consequences, while misuse for malicious activities can result in criminal charges. Additionally, aggressive scanning techniques can disrupt network operations and cause unwanted attention.
Tips for Using Nmap Effectively
- Start with basic scans: Begin with simple scans to gather initial information about the network, such as host discovery and port scanning.
- Use appropriate scan types: Choose scan types that balance speed, stealth, and information gathering based on your needs and the network’s security posture.
- Utilize Nmap’s script library: Leverage Nmap’s extensive script library for automated vulnerability checks, service fingerprinting, and other advanced tasks.
- Analyze and interpret results: Carefully analyze Nmap’s output to identify potential vulnerabilities, security risks, and network configuration issues.
- Document your findings: Maintain detailed records of your scans and findings for future reference and reporting.
Conclusion
Nmap is a powerful and versatile tool for network exploration, security auditing, and vulnerability assessment. While it can be misused for malicious activities, Nmap offers valuable applications for legitimate purposes, such as network administration, security testing, and research. By understanding Nmap’s capabilities, ethical considerations, and best practices, individuals and organizations can leverage its power responsibly and effectively to enhance network security and protect critical information.


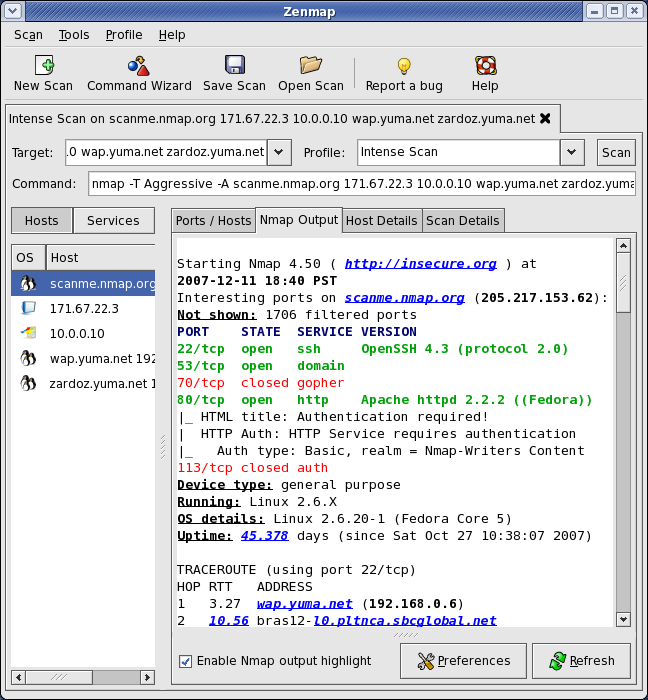
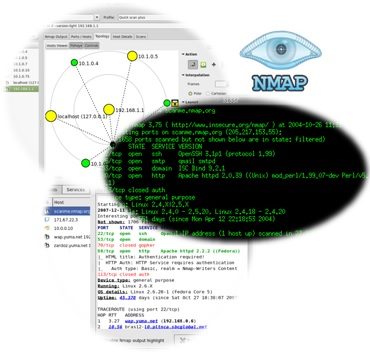


Closure
Thus, we hope this article has provided valuable insights into Nmap: A Powerful Tool for Network Exploration and Security Auditing. We hope you find this article informative and beneficial. See you in our next article!