The Essential Role of Secure and Reliable Software: A Comprehensive Exploration of Software Assurance
Related Articles: The Essential Role of Secure and Reliable Software: A Comprehensive Exploration of Software Assurance
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Essential Role of Secure and Reliable Software: A Comprehensive Exploration of Software Assurance. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Essential Role of Secure and Reliable Software: A Comprehensive Exploration of Software Assurance

In today’s digitally interconnected world, software permeates every aspect of our lives. From the applications we use on our smartphones to the complex systems that manage critical infrastructure, software has become an indispensable element of modern society. However, with this ubiquity comes a crucial need for assurance – a guarantee that the software we rely on is secure, reliable, and operates as intended.
This exploration delves into the multifaceted concept of software assurance, examining its core principles, benefits, and practical implications. We will explore the diverse factors that contribute to robust software assurance, including secure development practices, rigorous testing, and ongoing vulnerability management.
Understanding the Foundation: What is Software Assurance?
Software assurance encompasses a broad spectrum of practices and methodologies designed to ensure the quality, security, and reliability of software throughout its lifecycle. It goes beyond mere functionality, aiming to instill confidence in the software’s trustworthiness, resilience, and ability to withstand potential threats.
The Multifaceted Pillars of Software Assurance
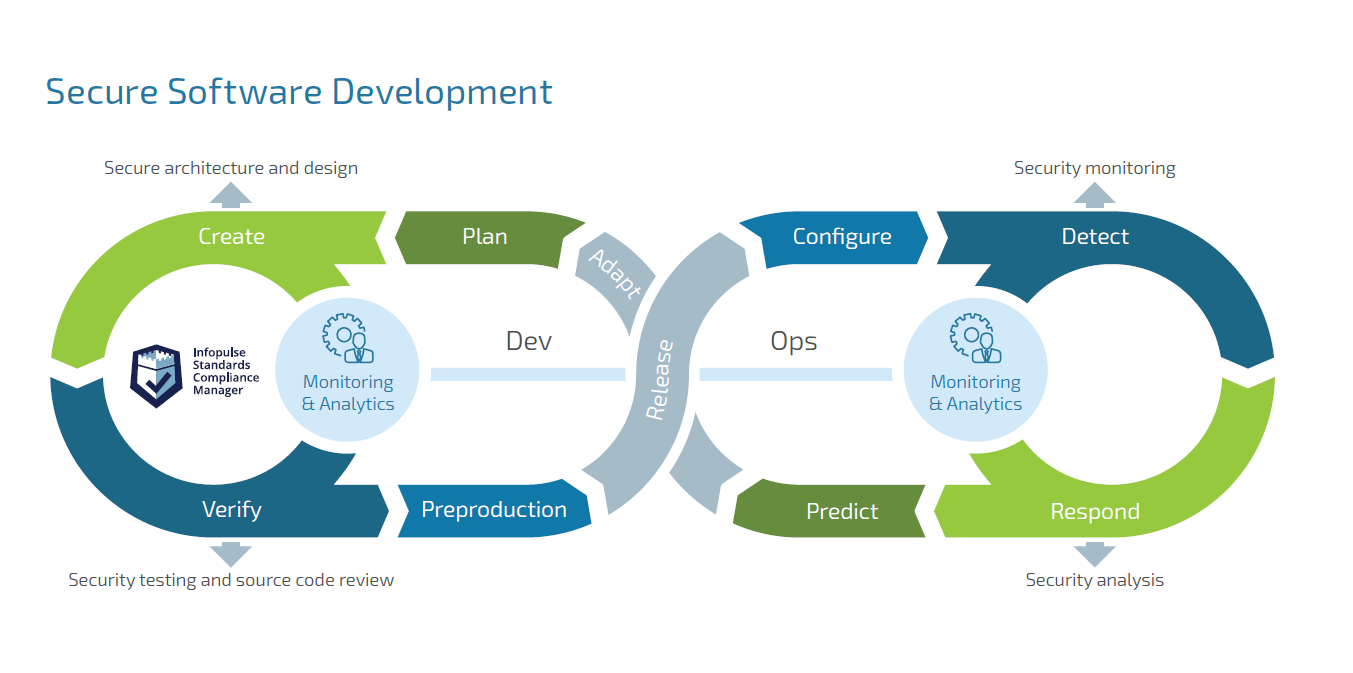
1. Secure Development Practices:
- Secure by Design: Incorporating security considerations from the very inception of the software development process. This involves proactively identifying and mitigating vulnerabilities before they are introduced into the codebase.
- Code Analysis and Review: Employing static and dynamic analysis tools to detect potential security flaws and vulnerabilities within the code.
- Secure Coding Standards: Adhering to established guidelines and best practices for writing secure code, minimizing the risk of introducing vulnerabilities.
- Threat Modeling: Proactively identifying potential threats and attack vectors, enabling developers to implement appropriate safeguards.
2. Rigorous Testing:
- Functional Testing: Ensuring that the software meets its intended functionality and performs as expected.
- Security Testing: Evaluating the software’s resistance to various security threats, such as penetration testing, vulnerability scanning, and fuzzing.
- Performance Testing: Assessing the software’s performance under various conditions, ensuring it meets required speed, responsiveness, and scalability.
- Usability Testing: Evaluating the software’s ease of use and user experience, ensuring it is intuitive and accessible.
3. Vulnerability Management:
- Continuous Monitoring: Actively scanning for and identifying vulnerabilities in the software, both known and unknown.
- Patch Management: Promptly applying security patches and updates to address identified vulnerabilities.
- Incident Response: Establishing clear procedures for responding to security incidents, mitigating damage, and preventing future occurrences.
- Vulnerability Disclosure: Establishing transparent communication channels for disclosing vulnerabilities to developers and users.
The Importance of Software Assurance
The benefits of robust software assurance extend far beyond technical considerations, impacting individuals, organizations, and society as a whole:
- Enhanced Security: Minimizing the risk of data breaches, unauthorized access, and other security threats.
- Increased Reliability: Ensuring that software functions consistently and reliably, minimizing downtime and disruptions.
- Improved Trust: Building confidence in the software’s trustworthiness and integrity, fostering user adoption and loyalty.
- Reduced Costs: Mitigating the financial costs associated with security breaches, software failures, and legal liabilities.
- Compliance with Regulations: Meeting regulatory requirements for data privacy, security, and compliance.
Addressing the Concerns: Frequently Asked Questions
Q: How can I ensure that my software is secure?
A: Implement a comprehensive software assurance program that encompasses secure development practices, rigorous testing, and ongoing vulnerability management.
Q: What are the key elements of a successful software assurance program?
A: A successful program involves:
- Commitment from leadership: Establishing clear policies and procedures for software assurance.
- Skilled personnel: Employing developers, testers, and security professionals with expertise in software assurance.
- Robust tools and technologies: Utilizing advanced tools for code analysis, security testing, and vulnerability management.
- Continuous improvement: Regularly reviewing and updating the program to adapt to evolving threats and best practices.
Q: What are some common software vulnerabilities?
A: Common vulnerabilities include:
- Cross-site scripting (XSS): Exploiting vulnerabilities in web applications to inject malicious scripts.
- SQL injection: Exploiting vulnerabilities in database queries to gain unauthorized access to data.
- Buffer overflows: Exploiting vulnerabilities in memory management to execute malicious code.
- Authentication and authorization flaws: Exploiting vulnerabilities in user authentication and authorization mechanisms.
Q: How can I stay informed about emerging software security threats?
A: Stay informed through:
- Industry publications and websites: Following reputable security news sources.
- Security conferences and webinars: Attending industry events to learn about latest threats and best practices.
- Security communities and forums: Engaging with security experts and practitioners to share knowledge and insights.
Guiding Principles: Tips for Enhancing Software Assurance
- Prioritize Security: Integrate security considerations into every phase of the software development lifecycle.
- Embrace Automation: Utilize automated tools for code analysis, security testing, and vulnerability management.
- Foster Collaboration: Encourage communication and collaboration between development, security, and operations teams.
- Stay Updated: Continuously monitor emerging security threats and update your software assurance practices accordingly.
- Measure and Improve: Track key metrics to assess the effectiveness of your software assurance program and identify areas for improvement.
Conclusion: A Foundation for Trust and Resilience
Software assurance is not a mere technical requirement; it is a fundamental principle that underpins the trustworthiness and resilience of our digital world. By prioritizing secure development practices, rigorous testing, and ongoing vulnerability management, we can build a foundation of trust and confidence in the software we rely on.
In a world increasingly dependent on software, embracing a comprehensive approach to software assurance is no longer an option; it is a necessity. By investing in robust assurance practices, we can mitigate risks, safeguard our digital assets, and ensure that software continues to serve as a catalyst for progress and innovation.







Closure
Thus, we hope this article has provided valuable insights into The Essential Role of Secure and Reliable Software: A Comprehensive Exploration of Software Assurance. We appreciate your attention to our article. See you in our next article!