The Power of Omission: Understanding Nmap’s -n Flag
Related Articles: The Power of Omission: Understanding Nmap’s -n Flag
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Power of Omission: Understanding Nmap’s -n Flag. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Power of Omission: Understanding Nmap’s -n Flag
- 2 Introduction
- 3 The Power of Omission: Understanding Nmap’s -n Flag
- 3.1 The Essence of -n: Avoiding Reverse DNS Resolution
- 3.2 The Benefits of -n: Efficiency and Discretion
- 3.3 Understanding the Trade-offs: Information vs. Speed
- 3.4 Nmap -n: FAQs
- 3.5 Nmap -n: Tips
- 3.6 Conclusion: The Power of Selective Omission
- 4 Closure
The Power of Omission: Understanding Nmap’s -n Flag
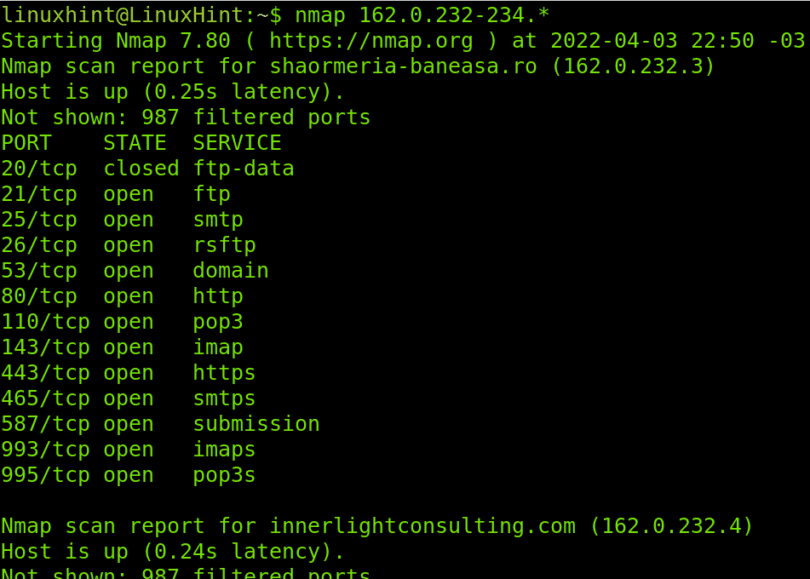
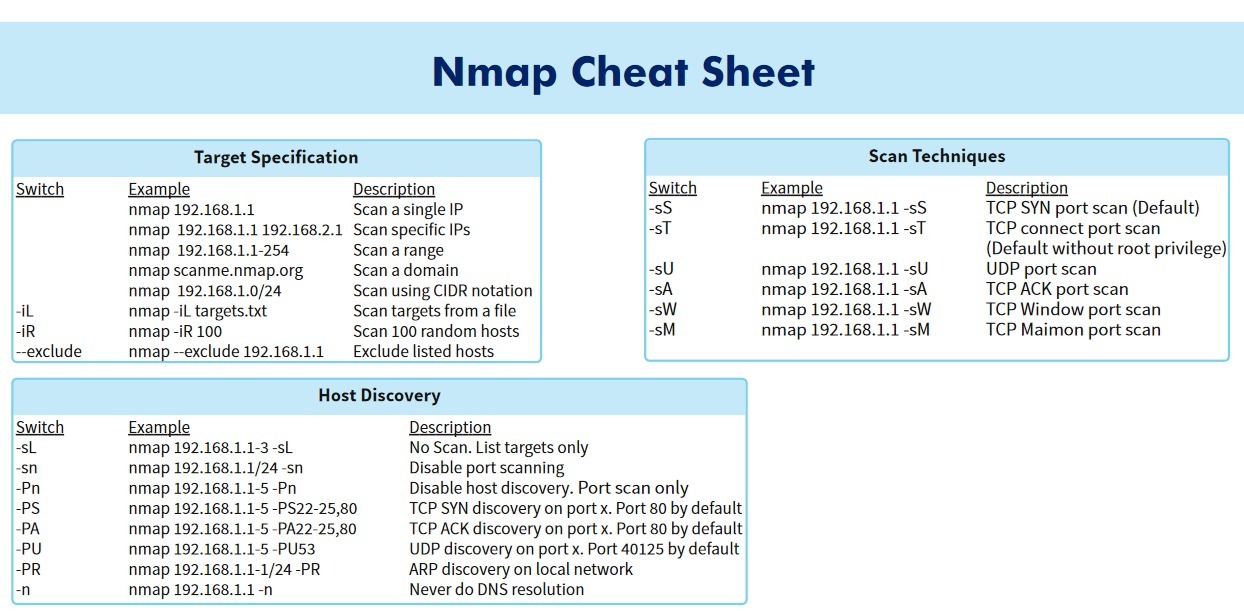
Network scanning is a fundamental practice in cybersecurity, network administration, and penetration testing. It involves systematically probing a network or host for active services, open ports, and potential vulnerabilities. Nmap, the Network Mapper, stands as a powerful and versatile tool for this purpose, offering a wide array of options and flags to tailor scans to specific needs. Among these, the -n flag, while seemingly simple, plays a crucial role in optimizing scan efficiency and minimizing network noise.
The Essence of -n: Avoiding Reverse DNS Resolution
At its core, the -n flag instructs Nmap to skip reverse DNS resolution during a scan. This seemingly minor omission significantly impacts the scan’s speed and behavior.
By default, Nmap attempts to resolve the IP addresses it encounters into their corresponding domain names using reverse DNS lookups. This process, while providing valuable information about the target system’s identity, can introduce considerable overhead, especially in large-scale scans or when dealing with networks containing numerous hosts.
Consider the following scenario:
Imagine scanning a network with hundreds of hosts. Nmap, by default, would attempt to perform a reverse DNS lookup for each IP address, potentially contacting numerous DNS servers and adding significant latency to the scan.
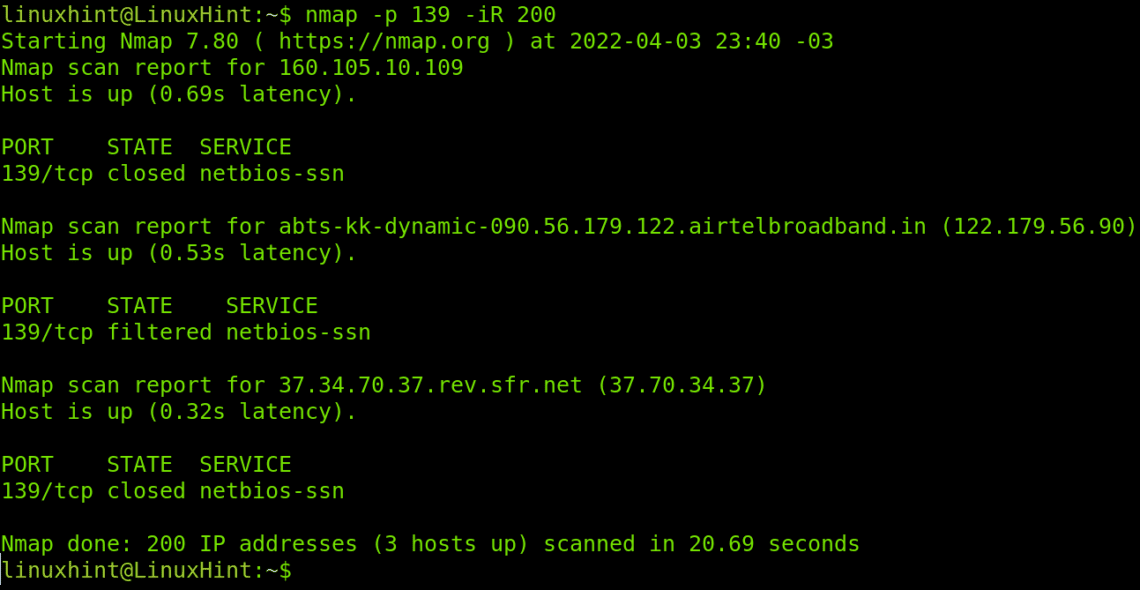
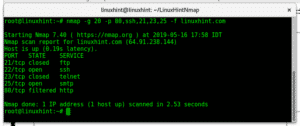
Here’s where -n comes into play. By specifying the -n flag, you instruct Nmap to bypass this step, focusing solely on the IP addresses themselves. This results in a faster and more efficient scan, especially when dealing with large networks or when speed is paramount.
The Benefits of -n: Efficiency and Discretion
The -n flag offers several tangible benefits, making it an invaluable tool for network professionals and security researchers:
-
Increased Scan Speed: The most immediate benefit of
-nis its ability to accelerate scans significantly. By eliminating the time-consuming process of reverse DNS lookups, Nmap can complete scans much faster, enabling quicker identification of open ports and services. - Reduced Network Traffic: The omission of reverse DNS queries also reduces the amount of network traffic generated by the scan. This is particularly beneficial in scenarios where bandwidth is limited or when minimizing network noise is crucial.
-
Enhanced Discretion: In certain situations, it’s desirable to conduct scans without generating excessive network traffic or revealing the identities of target systems. By suppressing reverse DNS lookups, the
-nflag helps maintain a lower profile, making it suitable for reconnaissance or covert operations. -
Focus on Core Information: By focusing solely on IP addresses and port information, the
-nflag simplifies scan output, making it easier to analyze and extract critical information.
Understanding the Trade-offs: Information vs. Speed
While the -n flag offers significant advantages, it’s essential to acknowledge the trade-offs involved. By skipping reverse DNS resolution, you sacrifice the ability to obtain valuable information about the target system’s domain name and associated hostname.
In scenarios where identifying the target system’s identity is crucial, the -n flag may not be the most suitable option. However, for tasks such as port scanning, service detection, and vulnerability assessment, where speed and efficiency are paramount, the benefits of -n often outweigh the loss of hostname information.
Nmap -n: FAQs
Q: Can I still obtain hostname information after using the -n flag?
A: While -n prevents Nmap from performing reverse DNS lookups during the initial scan, you can still obtain hostname information afterward. This can be achieved by using separate tools like nslookup or dig to perform a reverse DNS lookup on the IP addresses obtained from the scan.
Q: Is the -n flag suitable for all types of Nmap scans?
A: While -n is generally beneficial for scans focused on port discovery and service detection, it may not be ideal for scans that rely heavily on hostname information, such as vulnerability assessments or network mapping.
Q: Are there any other Nmap flags that influence DNS resolution?
A: Yes, Nmap provides several flags related to DNS resolution:
- -R: Forces Nmap to perform reverse DNS lookups for all targets, even if they are already known.
- -r: Disables reverse DNS lookups altogether.
- -sL: Performs a "list scan," which only attempts to resolve IP addresses to hostnames without performing any port scans.
Nmap -n: Tips
-
Combine with other flags: The
-nflag can be combined with other Nmap flags to further optimize scans. For example,-n -T4combines the-nflag with the-T4flag for increased scan speed. -
Consider the scan purpose: Carefully evaluate the scan’s objective before deciding whether to use the
-nflag. If hostname information is critical, consider alternative approaches or use separate tools for DNS resolution. -
Use for large-scale scans: The
-nflag is particularly beneficial for large-scale scans, where the time savings and reduced network traffic can be significant.
Conclusion: The Power of Selective Omission
The -n flag in Nmap provides a powerful mechanism for optimizing scans by selectively omitting reverse DNS resolution. By prioritizing speed and efficiency, it enables quicker identification of open ports and services, minimizing network traffic and enhancing scan discretion. While sacrificing hostname information, the -n flag remains a valuable tool for network professionals and security researchers, particularly when dealing with large networks or when speed is paramount. By understanding the trade-offs involved and carefully considering the scan’s objective, you can leverage the -n flag effectively to streamline your network scanning operations.


Closure
Thus, we hope this article has provided valuable insights into The Power of Omission: Understanding Nmap’s -n Flag. We appreciate your attention to our article. See you in our next article!