Understanding the Significance of Bitmaps and Masks in Computing
Related Articles: Understanding the Significance of Bitmaps and Masks in Computing
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Understanding the Significance of Bitmaps and Masks in Computing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Understanding the Significance of Bitmaps and Masks in Computing
- 2 Introduction
- 3 Understanding the Significance of Bitmaps and Masks in Computing
- 3.1 Bitmaps: A Foundation for Data Representation
- 3.1.1 Advantages of Bitmaps:
- 3.1.2 Common Applications of Bitmaps:
- 3.2 Masks: Precision Tools for Bit Manipulation
- 3.2.3 Types of Masks:
- 3.2.4 Applications of Masks:
- 3.3 Combining Bitmaps and Masks: A Powerful Partnership
- 3.3.5 Examples of Combined Usage:
- 3.4 FAQs on Bitmaps and Masks:
- 3.5 Tips for Effective Use of Bitmaps and Masks:
- 3.6 Conclusion:
- 4 Closure
Understanding the Significance of Bitmaps and Masks in Computing

In the realm of computing, the manipulation of data at its most fundamental level is crucial for achieving efficient and optimized operations. Bitmaps, as representations of data using individual bits, and masks, as tools for selectively modifying these bits, play a pivotal role in this process. This article delves into the intricacies of bitmaps and masks, exploring their functionalities, applications, and the profound impact they have on various computing domains.
Bitmaps: A Foundation for Data Representation
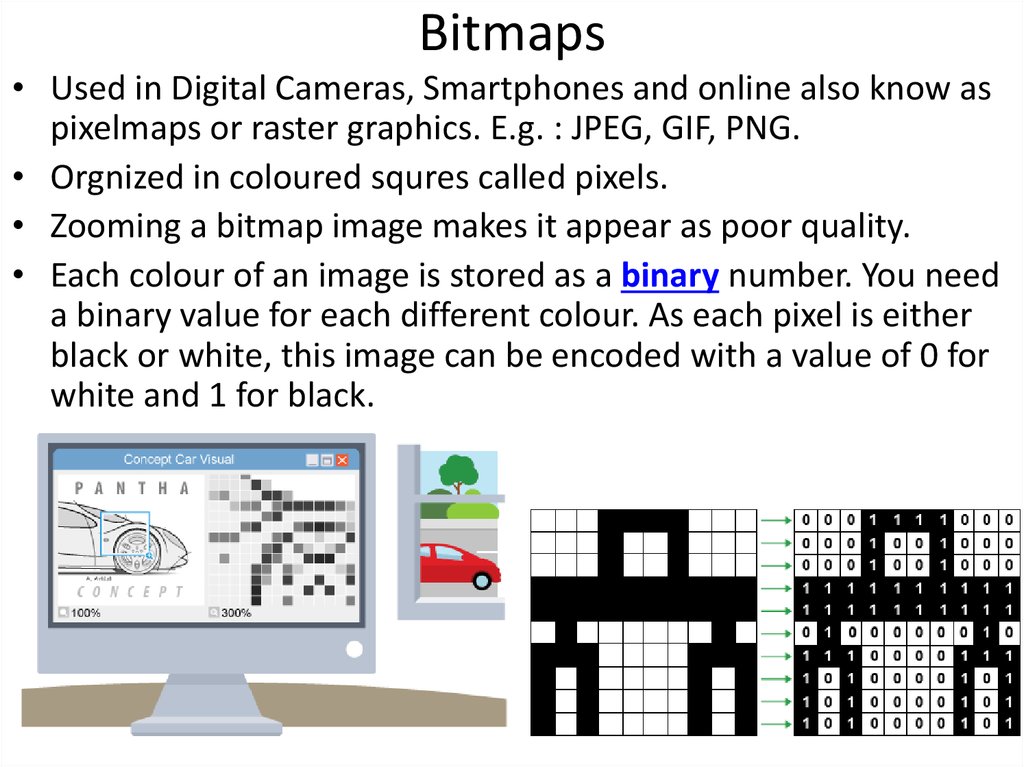
A bitmap, in essence, is a digital representation of data that utilizes a sequence of bits, each capable of holding a value of either 0 or 1. These bits, arranged in a specific order, collectively encode information. The interpretation of these bits depends on the context, ranging from simple binary representations to intricate representations of images, sounds, or even complex data structures.
Advantages of Bitmaps:
- Efficiency: Bitmaps are inherently efficient due to their compact nature, requiring minimal storage space. This efficiency is particularly advantageous in scenarios where data volume is significant, such as image processing or large-scale databases.
- Flexibility: Bitmaps offer remarkable flexibility in representing diverse types of data. The arrangement and interpretation of bits can be tailored to accommodate specific data structures and formats, making them adaptable to various applications.
- Direct Manipulation: Bitmaps allow for direct manipulation of individual bits, providing granular control over data representation and modification. This feature is invaluable in tasks requiring precise manipulation of data at the bit level.
Common Applications of Bitmaps:
- Image Representation: Digital images are commonly represented using bitmaps, where each bit corresponds to a pixel’s color value.
- Data Compression: Bitmaps are utilized in data compression algorithms to efficiently encode and store data, reducing storage requirements and transmission bandwidth.
- Network Communication: Bitmaps are employed in network protocols to represent data packets, facilitating the transmission and reception of information over networks.
- Memory Management: Bitmaps are used in memory management systems to track the availability of memory blocks, enabling efficient allocation and deallocation of resources.
Masks: Precision Tools for Bit Manipulation
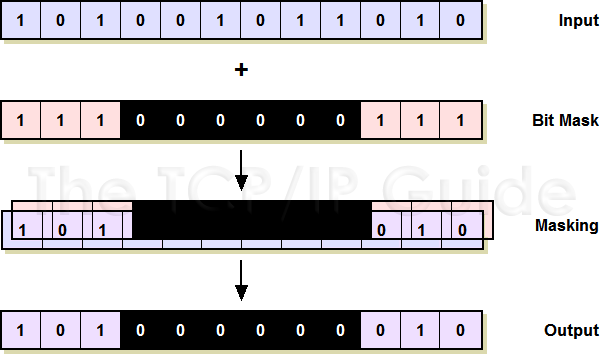
Masks, in the context of bitmaps, act as filters or templates that selectively modify the bits within a bitmap. They are typically represented as binary sequences, where each bit corresponds to a specific bit position in the bitmap. The mask’s bits determine which bits in the bitmap are affected during an operation.
Types of Masks:
- AND Mask: An AND mask is used to clear specific bits in a bitmap. The resulting bitmap retains only the bits that are set to 1 in both the original bitmap and the mask.
- OR Mask: An OR mask is used to set specific bits in a bitmap. The resulting bitmap contains all the bits that are set to 1 in either the original bitmap or the mask.
- XOR Mask: An XOR mask is used to toggle specific bits in a bitmap. The resulting bitmap has bits set to 1 where the original bitmap and mask have differing values.
- NOT Mask: A NOT mask inverts all the bits in a bitmap, changing 0s to 1s and vice versa.
Applications of Masks:
- Data Extraction: Masks can be used to extract specific data from a bitmap, isolating desired information.
- Data Modification: Masks enable the targeted modification of bits within a bitmap, allowing for precise manipulation of data.
- Data Validation: Masks can be used to validate data integrity by comparing the masked bits with expected values.
- Security: Masks play a crucial role in cryptography, where they are used to encrypt and decrypt data, ensuring data confidentiality and integrity.
Combining Bitmaps and Masks: A Powerful Partnership
The true power of bitmaps lies in their combination with masks. This synergy allows for efficient and precise manipulation of data at the bit level. By applying masks to bitmaps, we can isolate, modify, and extract specific data elements, achieving results that would be cumbersome or impossible with traditional methods.
Examples of Combined Usage:
- Image Editing: Masks are used in image editing software to isolate specific regions of an image, enabling selective modifications such as color adjustments or applying filters.
- Network Packet Filtering: Masks are used in network routers and firewalls to filter network traffic based on specific criteria, allowing only authorized packets to pass through.
- Database Queries: Masks are employed in database systems to filter data based on specific criteria, retrieving only the desired information.
FAQs on Bitmaps and Masks:
1. What is the difference between a bitmap and a mask?
A bitmap is a representation of data using bits, while a mask is a template used to modify specific bits within a bitmap.
2. How do masks work with bitmaps?
Masks are applied to bitmaps using logical operations such as AND, OR, XOR, or NOT. The mask’s bits determine which bits in the bitmap are affected during the operation.
3. What are some real-world applications of bitmaps and masks?
Bitmaps and masks are used in image editing, network communication, data compression, database management, and cryptography.
4. Are there any limitations to using bitmaps and masks?
While powerful, bitmaps and masks are not without limitations. They require a thorough understanding of bit manipulation and can be complex to implement in certain scenarios.
5. How can I learn more about bitmaps and masks?
Numerous resources are available online and in textbooks covering the concepts of bitmaps and masks. Exploring programming languages like C, C++, and Python can provide practical experience with these concepts.
Tips for Effective Use of Bitmaps and Masks:
- Understand the Data Structure: Before manipulating bitmaps, it is crucial to understand the data structure and the meaning of each bit.
- Use Appropriate Masks: Select the appropriate mask based on the desired operation and the specific bits you want to modify.
- Avoid Overlapping Masks: Ensure that masks do not overlap, as this can lead to unintended consequences.
- Test Thoroughly: Thoroughly test your code to ensure that bitmaps and masks are working as expected.
Conclusion:
Bitmaps and masks are fundamental tools in the realm of computing, enabling efficient and precise manipulation of data at the bit level. Their applications span various domains, from image processing and network communication to cryptography and database management. Understanding these concepts and their functionalities is essential for anyone seeking to optimize data handling, streamline operations, and unlock the full potential of computing resources.





Closure
Thus, we hope this article has provided valuable insights into Understanding the Significance of Bitmaps and Masks in Computing. We hope you find this article informative and beneficial. See you in our next article!
