Unlocking Network Insights: A Comprehensive Guide to Nmap’s Port Scanning Capabilities
Related Articles: Unlocking Network Insights: A Comprehensive Guide to Nmap’s Port Scanning Capabilities
Introduction
With great pleasure, we will explore the intriguing topic related to Unlocking Network Insights: A Comprehensive Guide to Nmap’s Port Scanning Capabilities. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking Network Insights: A Comprehensive Guide to Nmap’s Port Scanning Capabilities

Network security professionals and system administrators rely heavily on network scanning tools to gain valuable insights into the systems and services operating within their network. Among the most popular and powerful tools is Nmap, renowned for its versatility and comprehensive scanning capabilities. This article delves into the intricacies of Nmap’s port scanning techniques, focusing on the "fast scan" functionality and its applications in network security assessments.
Understanding the Essence of Port Scanning
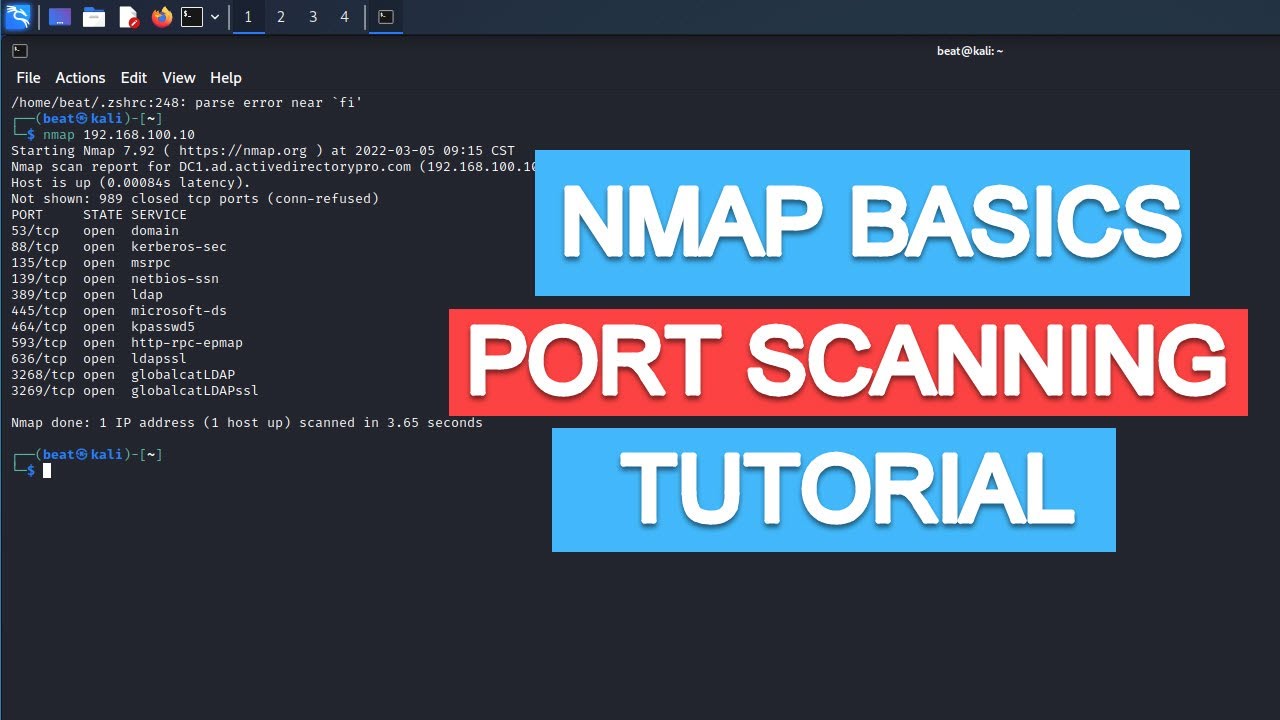
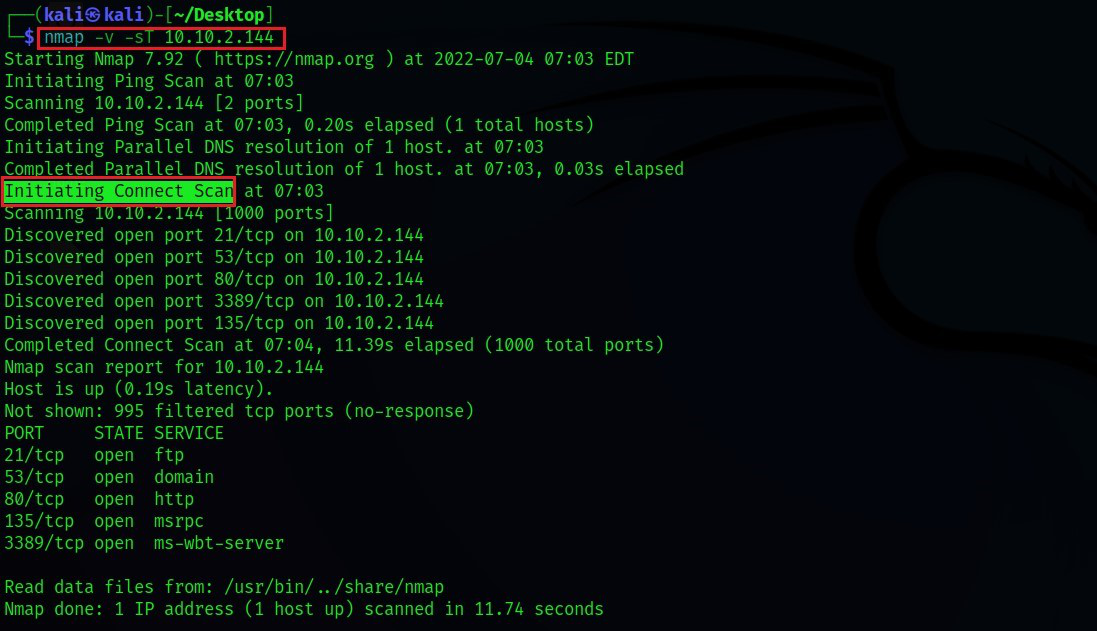
Port scanning is a fundamental technique in network security analysis. It involves probing network hosts for open ports, which are pathways through which applications and services communicate. Each port corresponds to a specific service, such as HTTP (port 80), SSH (port 22), or FTP (port 21). By identifying open ports, security professionals can glean crucial information about the services running on a host, potential vulnerabilities, and potential attack vectors.
Nmap’s Comprehensive Toolkit
Nmap offers a vast array of scanning options, catering to diverse security assessment needs. Its versatility stems from its ability to:
- Target Specific Hosts: Nmap allows users to scan individual hosts or entire networks, ensuring targeted analysis.
- Customize Scan Depth: From quick "ping scans" to in-depth "intense scans," Nmap provides granular control over the scope and intensity of the scan.
- Employ Multiple Scanning Techniques: Nmap supports various scanning methodologies, including TCP SYN, UDP, and ICMP, allowing for comprehensive exploration of network services.
- Generate Detailed Output: Nmap produces detailed reports, including open ports, service versions, operating systems, and potential vulnerabilities, facilitating informed decision-making.
The "Fast Scan" Functionality
While Nmap provides comprehensive scanning options, situations often arise where time is of the essence. This is where Nmap’s "fast scan" functionality proves invaluable. Designed for rapid network reconnaissance, the "fast scan" prioritizes speed over exhaustive port coverage. It focuses on the most common ports, typically associated with popular services, offering a swift overview of a host’s network presence.
Benefits of the "Fast Scan"
- Rapid Network Reconnaissance: The "fast scan" significantly reduces the time required to obtain a general understanding of a host’s network services.
- Initial Vulnerability Assessment: By identifying common ports, the "fast scan" provides a preliminary assessment of potential vulnerabilities, prompting further investigation if necessary.
- Efficient Network Monitoring: The "fast scan" serves as a valuable tool for routine network monitoring, detecting changes in open ports and potential security breaches.
- Resource Optimization: By focusing on essential ports, the "fast scan" minimizes network traffic and resource consumption, making it ideal for large-scale scans or resource-constrained environments.
Implementing the "Fast Scan"
Nmap’s "fast scan" is easily implemented using the "-F" flag. For instance, to perform a fast scan on the host "192.168.1.100," the following command can be used:
nmap -F 192.168.1.100This command will scan the host for the most common ports, providing a quick overview of its network services.
Beyond the "Fast Scan"
While the "fast scan" offers a rapid overview, comprehensive network security assessments often require more in-depth analysis. Nmap provides a range of additional options for customizing scans:
- -T4: This flag sets the scan speed to "aggressive," maximizing scanning speed.
- -p 1-1024: This flag specifies a range of ports to scan, allowing for focused analysis on specific port ranges.
- -sV: This flag enables service version detection, identifying the specific versions of services running on open ports.
- -O: This flag enables operating system detection, identifying the operating system running on the target host.
Addressing Common Questions
Q: What are the limitations of the "fast scan?"
A: The "fast scan" focuses on common ports, potentially overlooking less common ports associated with niche services. It might not detect all open ports or identify specific service versions.
Q: How does the "fast scan" impact network performance?
A: While the "fast scan" is designed for speed, it can still generate network traffic. It’s essential to consider the impact on network performance, especially in high-traffic environments.
Q: Can the "fast scan" be used for malicious purposes?
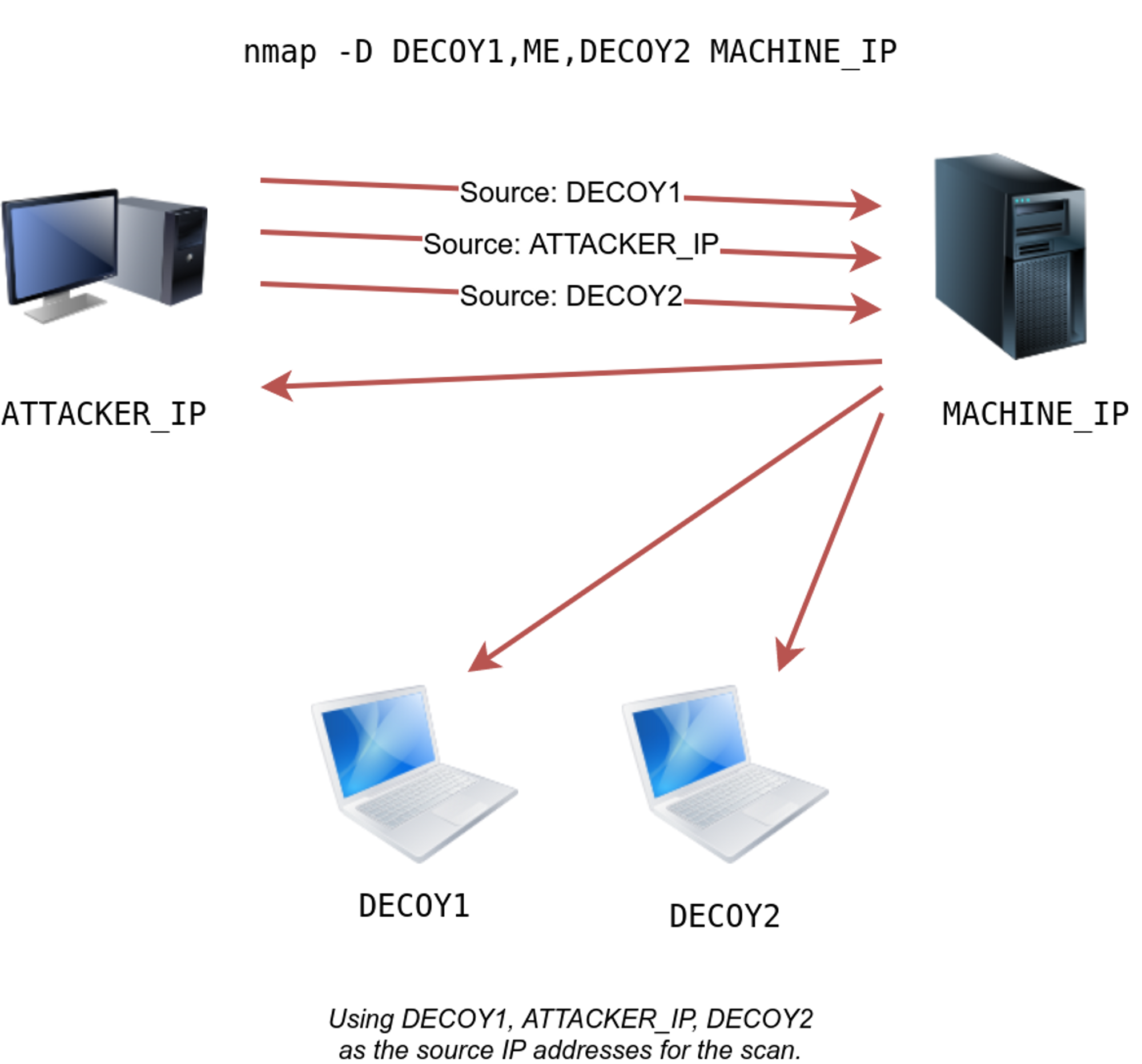
A: Like any network scanning tool, Nmap’s "fast scan" can be misused for malicious purposes. It’s crucial to use Nmap responsibly and ethically, respecting network security policies and obtaining appropriate permissions before scanning any network.
Tips for Effective Port Scanning with Nmap
- Define Scan Scope: Clearly define the scope of your scan, targeting specific hosts or network segments for efficient analysis.
- Optimize Scan Speed: Choose the appropriate scan speed based on your needs, balancing speed with thoroughness.
- Utilize Service and OS Detection: Enable service and operating system detection for comprehensive network insights.
- Analyze Output Carefully: Thoroughly review Nmap’s output, identifying open ports, service versions, and potential vulnerabilities.
- Document Findings: Maintain detailed records of your scan results for future reference and analysis.
Conclusion
Nmap’s "fast scan" functionality provides a powerful tool for rapid network reconnaissance and initial vulnerability assessment. It enables security professionals to gain a quick understanding of a host’s network services, identify potential vulnerabilities, and prioritize further investigation. By leveraging Nmap’s versatile scanning options and understanding its capabilities, security professionals can effectively assess network security posture, identify potential risks, and implement appropriate mitigation strategies. However, it’s crucial to use Nmap responsibly and ethically, adhering to network security policies and respecting the privacy of others.




Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Insights: A Comprehensive Guide to Nmap’s Port Scanning Capabilities. We thank you for taking the time to read this article. See you in our next article!
