Unlocking Network Intelligence: A Comprehensive Guide to Essential Nmap Flags
Related Articles: Unlocking Network Intelligence: A Comprehensive Guide to Essential Nmap Flags
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unlocking Network Intelligence: A Comprehensive Guide to Essential Nmap Flags. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking Network Intelligence: A Comprehensive Guide to Essential Nmap Flags
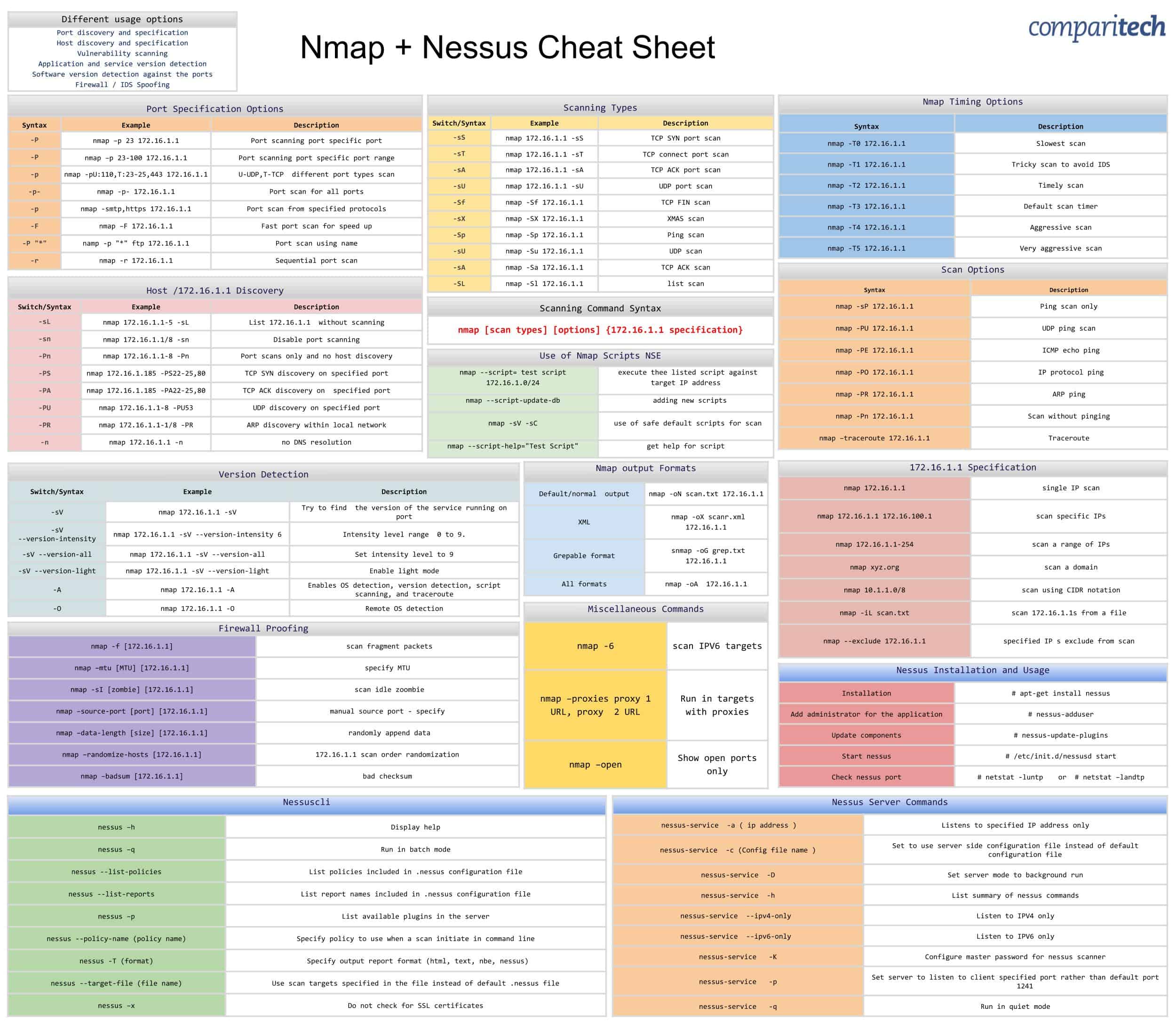
Nmap, the Network Mapper, is a powerful and versatile tool for network exploration and security auditing. Its flexibility lies in its extensive array of flags, each designed to modify its behavior and provide specific insights into a target network. This guide delves into the most essential Nmap flags, outlining their functionality and demonstrating their practical applications.
Essential Flags for Network Discovery and Host Identification
-
-sL (List Scan): This flag performs a simple "ping sweep" across a network range, identifying active hosts without attempting to determine open ports. Its efficiency makes it ideal for initial network reconnaissance or for quickly identifying active devices.
-
-sT (TCP Connect Scan): The TCP Connect Scan is a classic technique that establishes a full TCP connection to each port on a target host. It offers high accuracy in determining open ports but can be intrusive, potentially triggering security alerts.
-
-sU (UDP Scan): Similar to the TCP Connect Scan, the UDP Scan attempts to establish connections to UDP ports. However, its reliability is lower due to the nature of UDP, which doesn’t require a handshake.
-
-sS (SYN Scan): The SYN Scan, also known as a stealth scan, is a more discreet method that sends a SYN packet to each port, simulating a TCP handshake without completing the connection. This reduces the likelihood of detection by intrusion detection systems (IDS).
-
-sF (FIN Scan): The FIN Scan is another stealthy technique that sends a FIN packet to each port. It is particularly effective at bypassing firewalls that filter SYN packets but may not be reliable in identifying open ports.
-
-sN (Null Scan): The Null Scan sends a packet with all flags set to zero, relying on the target host’s response to determine open ports. It is highly stealthy but may not be reliable for all operating systems.
-
-sX (Xmas Scan): The Xmas Scan sends a packet with the FIN, PSH, and URG flags set, relying on the target host’s response to determine open ports. Similar to the Null Scan, it is stealthy but may not be reliable for all operating systems.
-
-Pn (No Ping): This flag instructs Nmap to skip the initial ping scan, allowing it to scan networks even if hosts are configured to block ICMP requests.
-
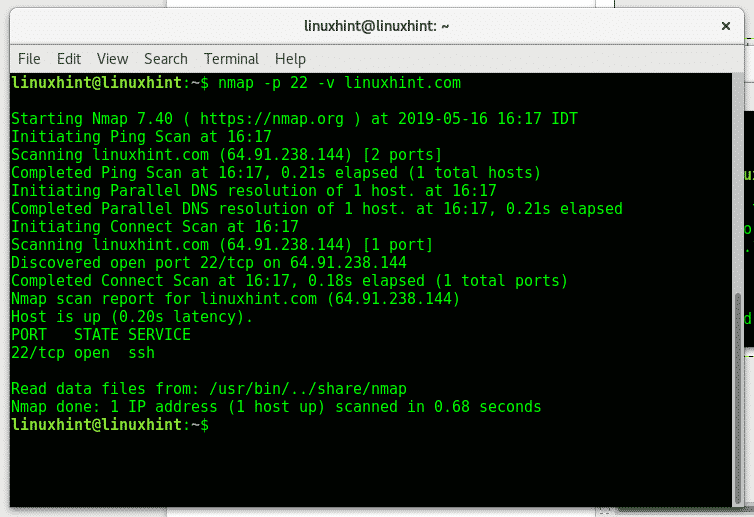
-p (Port Specification): The -p flag allows users to specify the ports to be scanned, either individually or as a range. This provides targeted analysis and reduces scan time.
-
-F (Fast Scan): The -F flag instructs Nmap to scan only the most common ports, offering a quick overview of potential vulnerabilities.
-
-T (Timing Template): Nmap allows users to customize scan speed and aggressiveness with timing templates. Options like -T4 (Aggressive) and -T0 (Paranoid) offer fine-grained control over scan behavior.
Flags for Service and Operating System Detection
-
-sV (Version Scan): This flag attempts to identify the services running on open ports and their versions. It provides valuable information for vulnerability analysis and exploit identification.
-
-O (Operating System Detection): The -O flag utilizes a sophisticated fingerprinting technique to identify the target host’s operating system. This information is crucial for understanding the target’s security posture and vulnerabilities.
-
-A (Aggressive Scan): This flag combines multiple flags, including -sV, -O, and -T4, to perform a comprehensive scan for services, operating systems, and potential vulnerabilities.
-
-Pn (No Ping): This flag is also essential for operating system detection, as it allows Nmap to scan networks even if hosts are configured to block ICMP requests.
Flags for Scripting and Advanced Functionality
-
-sC (Default Scripts): This flag executes Nmap’s default set of scripts, providing valuable insights into common vulnerabilities and misconfigurations.
-
-script (Script Selection): This flag allows users to execute specific scripts from Nmap’s extensive library. It enables targeted analysis for specific vulnerabilities or services.
-
-script-args (Script Arguments): This flag allows users to pass arguments to Nmap scripts, customizing their behavior and providing additional information.
-
-oX (XML Output): This flag generates output in XML format, which can be easily parsed and processed by other tools or scripts.
-
-oA (All Output): This flag saves all output formats, including normal, XML, and greppable, for comprehensive analysis.
-
-iL (Input File): This flag allows users to load target lists from external files, enabling efficient scanning of large networks or complex targets.
-
-oN (Normal Output): This flag generates output in a plain text format, suitable for basic analysis and reporting.
-
-oG (Greppable Output): This flag generates output in a greppable format, facilitating easy filtering and analysis of specific data.
FAQs about Nmap Flags
-
Q: What is the difference between -sT and -sS?
- A: The TCP Connect Scan (-sT) establishes a full TCP connection, while the SYN Scan (-sS) only sends a SYN packet, making it more stealthy.
-
Q: How do I identify the services running on a target host?
- A: Use the -sV flag to perform a version scan, which attempts to identify services and their versions.
-
Q: Can Nmap be used to scan networks behind firewalls?
- A: Nmap can scan networks behind firewalls if the firewall allows the necessary traffic. However, it may require advanced techniques like port forwarding or proxy servers.
-
Q: What are the best flags for security auditing?
- A: A combination of flags like -sV, -O, -sC, and -script can provide comprehensive information for security auditing.
Tips for Effective Nmap Usage
- Start with basic scans: Begin with simple scans like -sL or -F to get an initial understanding of the network.
- Use stealthy techniques: Employ flags like -sS or -sN for discreet scanning, especially in environments with intrusion detection systems.
- Customize scan speed: Utilize timing templates like -T4 or -T0 to adjust scan speed based on network size and security requirements.
- Utilize scripts: Leverage Nmap’s extensive script library for targeted analysis and vulnerability identification.
- Document your findings: Record scan results for future reference and analysis.
Conclusion
Nmap’s diverse set of flags empowers users to tailor their network scanning efforts to specific needs and objectives. By leveraging the right combination of flags, users can gain valuable insights into network topology, host characteristics, running services, and potential vulnerabilities. This knowledge is essential for network administrators, security professionals, and anyone seeking to understand and secure their network environment.


![]()

Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Intelligence: A Comprehensive Guide to Essential Nmap Flags. We appreciate your attention to our article. See you in our next article!