Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities
Related Articles: Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities
Introduction
With great pleasure, we will explore the intriguing topic related to Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities
- 2 Introduction
- 3 Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities
- 3.1 Understanding Hashing: The Foundation of Network Security
- 3.2 Nmap’s Hashing Capabilities: A Multifaceted Tool
- 3.3 Applications of Nmap Hashing: Unlocking Insights and Securing Networks
- 3.4 Utilizing Nmap’s Hashing Capabilities: Practical Examples
- 3.5 FAQs: Addressing Common Questions about Nmap Hashing
- 3.6 Tips for Utilizing Nmap’s Hashing Capabilities Effectively
- 3.7 Conclusion: Nmap’s Hashing Capabilities – A Vital Tool for Network Security
- 4 Closure
Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities

Nmap, the Network Mapper, is a powerful and versatile tool used by network administrators, security professionals, and researchers to scan and analyze networks. While renowned for its port scanning capabilities, Nmap offers a lesser-known but equally valuable feature: hashing. This article delves into the world of Nmap hashing, exploring its various applications, benefits, and techniques.
Understanding Hashing: The Foundation of Network Security
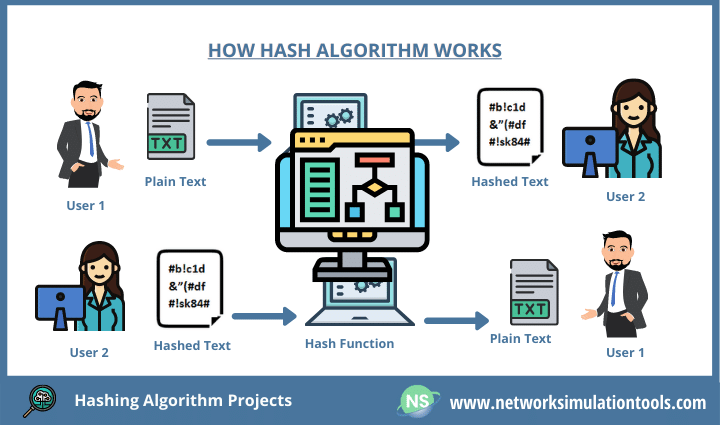
Hashing is a fundamental cryptographic technique that converts any data, regardless of size, into a fixed-length string of characters known as a hash. This process is irreversible, meaning it’s impossible to reconstruct the original data from its hash. The key properties of a hash function are:
- Deterministic: A specific input always generates the same hash output.
- One-way: It’s computationally infeasible to reverse the hashing process.
- Collision resistance: It’s highly unlikely that two different inputs will produce the same hash.
These properties make hashing indispensable for various security applications, including:
- Password storage: Storing passwords directly is a security risk. Hashing passwords ensures that even if a database is compromised, attackers cannot access the original passwords.
- Data integrity verification: Hashing allows verifying the integrity of data by comparing the hash of the original data with the hash of the received data. Any discrepancy indicates tampering.
- Digital signatures: Hashing plays a crucial role in digital signatures, ensuring the authenticity and integrity of digital documents.
Nmap’s Hashing Capabilities: A Multifaceted Tool
Nmap incorporates hashing capabilities, enhancing its network analysis and security auditing capabilities. It leverages various hashing algorithms, each with specific strengths and applications:
- MD5: A widely used algorithm, although its security has been compromised due to its vulnerability to collisions.
- SHA-1: Another popular algorithm, but it is considered outdated due to its susceptibility to collision attacks.
- SHA-256: A stronger and more secure algorithm recommended for most applications.
- SHA-512: A highly secure algorithm, offering the highest level of protection against collisions.
Applications of Nmap Hashing: Unlocking Insights and Securing Networks
Nmap’s hashing capabilities find diverse applications in network security and analysis:
1. Network Fingerprint Identification:
Nmap’s fingerprint scanning technique leverages hashing to identify and categorize network devices. By comparing the hash of a device’s response to known signatures, Nmap can accurately identify the operating system, device type, and even specific software versions. This information is invaluable for network administrators, allowing them to:
- Inventory network assets: Track and manage all devices connected to the network.
- Identify vulnerabilities: Discover potential security weaknesses based on known vulnerabilities associated with specific device types or software versions.
- Optimize network configuration: Tailor network configurations to specific device types for improved performance and security.
2. Service Identification and Version Detection:
Nmap’s service detection relies on hashing to identify running services on network devices. By comparing the hash of a service’s response to a database of known service signatures, Nmap can accurately determine the service type, version, and even the specific software used. This information is crucial for:
- Network security auditing: Identify potentially vulnerable services that require patching or configuration changes.
- Service monitoring: Track the availability and status of critical services on the network.
- Application analysis: Gain insight into the applications running on network devices, aiding in troubleshooting and optimization.
3. Data Integrity Verification:
Nmap can be used to verify the integrity of data transferred over the network. By comparing the hash of the original data with the hash of the received data, Nmap can detect any modifications or tampering. This feature is particularly useful for:
- File transfer security: Ensuring the integrity of files transferred across the network.
- Network traffic analysis: Detecting potential data manipulation or injection attacks.
- Security auditing: Verifying the integrity of critical network configurations and data files.
4. Password Hashing and Cracking:
While Nmap is not designed for password cracking, it can be used to identify and analyze password hashing algorithms used by network devices. This information can be valuable for:
- Security auditing: Assessing the strength of password security measures implemented on network devices.
- Vulnerability assessment: Identifying devices using weak or outdated password hashing algorithms that may be vulnerable to attacks.
- Password recovery: In limited scenarios, Nmap can be used to aid in password recovery efforts by identifying the hashing algorithm used and potentially attempting to crack the hash.
Utilizing Nmap’s Hashing Capabilities: Practical Examples
To leverage Nmap’s hashing capabilities, users can employ various options and techniques:
- -sV: This option enables Nmap to perform service detection and version determination, leveraging hashing to identify services running on target devices.
- -O: This option triggers Nmap’s operating system detection, utilizing hashing to identify the operating system running on target devices.
- -Pn: This option instructs Nmap to skip the host discovery phase, assuming all specified targets are online. This is useful when targeting devices that are already known to be online or when the host discovery process is undesirable.
- -F: This option instructs Nmap to perform a fast scan, limiting the number of ports scanned and reducing the time required for scanning. This is useful for quick checks or when speed is a priority.
- –script: This option allows users to execute custom scripts that can perform various network analysis and security auditing tasks, including hashing operations.
FAQs: Addressing Common Questions about Nmap Hashing
Q: What are the benefits of using Nmap’s hashing capabilities?
A: Nmap’s hashing capabilities offer several benefits, including:
- Enhanced network security: By identifying vulnerabilities and weaknesses, Nmap helps strengthen network security posture.
- Improved network visibility: Nmap provides valuable insights into network assets, services, and operating systems.
- Streamlined network management: Nmap’s detailed information aids in efficient network administration and troubleshooting.
Q: Are there any limitations to Nmap’s hashing capabilities?
A: While powerful, Nmap’s hashing capabilities have some limitations:
- Hashing algorithm selection: Nmap’s default hashing algorithms may not be suitable for all scenarios, requiring users to manually specify desired algorithms.
- Complexity of analysis: Interpreting and analyzing the output of Nmap’s hashing operations requires a certain level of technical expertise.
- Potential for false positives: While Nmap strives for accuracy, there is always a chance of false positives due to factors like network noise or outdated signatures.
Q: Can Nmap be used for password cracking?
A: While Nmap can identify the hashing algorithms used by network devices, it is not designed for password cracking. Dedicated password cracking tools are more suitable for this purpose.
Q: How can I learn more about Nmap’s hashing capabilities?
A: The Nmap documentation, available on the official Nmap website, provides detailed information on its various features, including hashing. Online forums and communities dedicated to Nmap also offer valuable resources and support.
Tips for Utilizing Nmap’s Hashing Capabilities Effectively
- Understand the limitations: Be aware of the limitations of Nmap’s hashing capabilities, especially regarding algorithm selection and potential for false positives.
- Use appropriate options: Select the appropriate Nmap options based on the specific task and desired level of detail.
- Leverage custom scripts: Explore custom Nmap scripts to extend its functionality and perform specific hashing operations.
- Consult documentation: Refer to the official Nmap documentation for detailed information on its features and options.
- Practice and experiment: Gain hands-on experience with Nmap’s hashing capabilities through practice and experimentation.
Conclusion: Nmap’s Hashing Capabilities – A Vital Tool for Network Security
Nmap’s hashing capabilities are a powerful tool for network administrators, security professionals, and researchers. By leveraging these capabilities, users can gain valuable insights into network assets, identify vulnerabilities, and improve network security posture. While Nmap is not a replacement for dedicated security tools, its hashing features complement a comprehensive security strategy, providing valuable information for informed decision-making and proactive security measures. As network security landscapes evolve, understanding and utilizing Nmap’s hashing capabilities is essential for safeguarding networks and mitigating potential threats.



Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Security: A Comprehensive Guide to Nmap’s Hashing Capabilities. We hope you find this article informative and beneficial. See you in our next article!