Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags
Related Articles: Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags
- 2 Introduction
- 3 Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags
- 3.1 Understanding Nmap’s Flag System
- 3.2 Essential Nmap Flags: A Foundation for Network Exploration
- 3.3 Exploring Nmap Flags: A Deeper Dive
- 3.3.1 Target Specification Flags: Defining the Scope
- 3.3.2 Scan Type Flags: Tailoring the Approach
- 3.3.3 Output Formatting Flags: Controlling the Presentation
- 3.3.4 Advanced Flags: Expanding the Capabilities
- 3.4 FAQs about Nmap Flags
- 3.5 Tips for Effective Nmap Usage
- 3.6 Conclusion
- 4 Closure
Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags

Nmap, the Network Mapper, is a powerful and versatile tool for network exploration and security auditing. Its command-line interface, while initially intimidating, unlocks a wealth of functionality through a system of flags. These flags act as modifiers, allowing users to fine-tune Nmap’s behavior, tailoring it to specific tasks and objectives. This guide delves into the diverse world of Nmap flags, providing a comprehensive understanding of their purpose, usage, and implications.
Understanding Nmap’s Flag System
Nmap flags are short, single-letter or multi-letter commands that precede the target IP address or hostname in the Nmap command. They influence various aspects of the scan, including:
- Target Selection: Defining the scope of the scan, specifying individual hosts, networks, or ranges.
- Scan Type: Choosing the type of scan to perform, from basic port scans to complex vulnerability checks.
- Output Formatting: Controlling how scan results are displayed, including text, XML, or other formats.
- Timing and Performance: Adjusting scan speed, timeout settings, and other performance-related parameters.
- Stealth and Evasion: Employing techniques to minimize detection and avoid triggering security systems.
Essential Nmap Flags: A Foundation for Network Exploration
1. Target Specification Flags:
- -T: Sets the timing template, influencing the speed of the scan. Higher values (e.g., -T4) result in faster scans, while lower values (e.g., -T1) prioritize stealth and minimize network impact.
- -F: Performs a "fast" scan, focusing on the most common ports. This can be useful for initial reconnaissance or when speed is paramount.
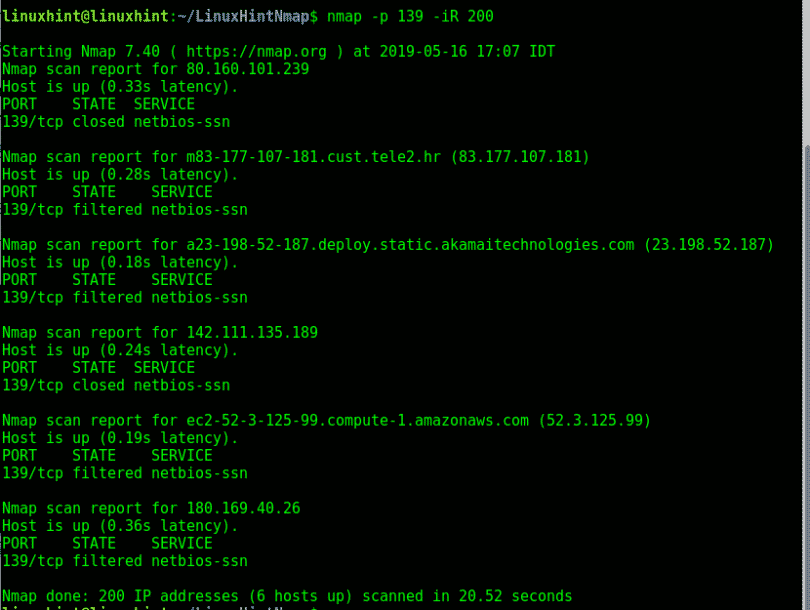
- -iR: Scans hosts listed in a file, allowing for batch scanning of multiple targets.
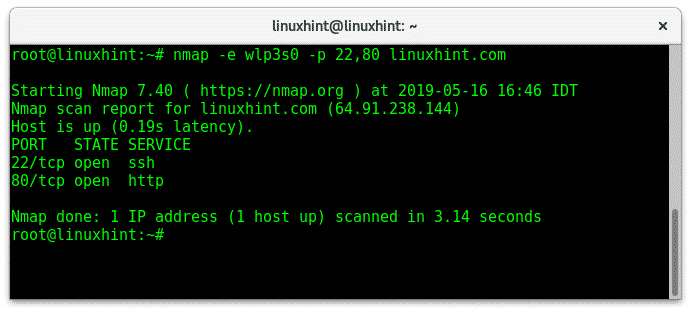
- -p: Specifies the ports to scan, allowing users to focus on specific ports of interest.
- -sL: Performs a "list scan," simply enumerating the targets without attempting to connect.
2. Scan Type Flags:
- -sT: Executes a TCP connect scan, attempting to establish a connection to each port. This is the most common and straightforward scan type.
- -sS: Conducts a SYN scan, sending SYN packets and analyzing the response to determine port status. This is a stealthier approach, as it does not fully establish a connection.
- -sU: Performs a UDP scan, probing UDP ports for open services.
- -sV: Attempts to identify the service running on each open port, providing valuable information about the target system.
- -sC: Runs a script scan, leveraging Nmap’s extensive library of scripts to perform vulnerability checks, banner grabbing, and other advanced analyses.
3. Output Formatting Flags:
- -oN: Saves the scan results to a normal text file.
- -oX: Outputs the results in XML format, allowing for easy parsing and integration with other tools.
- -oG: Generates an output in Grepable format, facilitating analysis with text-based tools like grep.
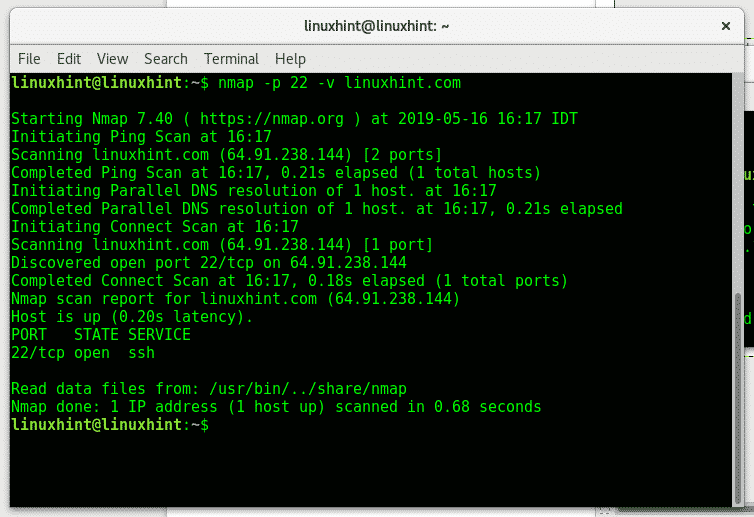
- -v: Increases the verbosity of the output, providing more detailed information about the scan process.
4. Advanced Flags:
- -A: Performs an "aggressive" scan, combining several scan types and scripts for comprehensive analysis.
- -D: Specifies a decoy list, sending probes from multiple IP addresses to obfuscate the scan origin.
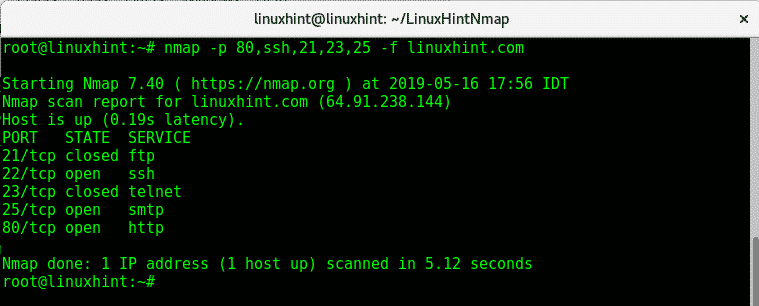
- -f: Fragments the packets, potentially evading firewalls or intrusion detection systems.
- -g: Uses a specific gateway for the scan, allowing for control over the network path.
- -M: Performs a "masscan" scan, leveraging a distributed network of machines to accelerate the scanning process.
Exploring Nmap Flags: A Deeper Dive
The following sections delve into specific categories of Nmap flags, providing in-depth explanations and practical examples.
Target Specification Flags: Defining the Scope
- -iL: Specifies a file containing a list of IP addresses or hostnames to scan. This flag enables efficient batch scanning of large target sets.
- -r: Reads target information from a previously saved scan output, allowing for re-scanning or analysis of previously identified hosts.
- -b: Specifies a subnet to scan, enabling comprehensive network mapping.
- -n: Disables reverse DNS resolution, speeding up the scan but reducing the information provided.
- -R: Enables reverse DNS resolution, providing hostnames for scanned IP addresses.
Example:
nmap -iL target_list.txt -T4 -p 22,80 -oN scan_results.txtThis command scans the IP addresses listed in "target_list.txt," using a fast timing template (-T4), focusing on ports 22 and 80, and saving the results to "scan_results.txt."
Scan Type Flags: Tailoring the Approach
- -sV: Attempts to identify the service running on each open port, providing valuable information about the target system.
- -sC: Runs a script scan, leveraging Nmap’s extensive library of scripts to perform vulnerability checks, banner grabbing, and other advanced analyses.
- -sI: Performs an idle scan, leveraging the network activity of other hosts to identify open ports without directly interacting with the target.
- -sX: Conducts a Xmas scan, sending a specific packet combination to identify open ports.
- -sN: Executes a null scan, sending packets with the null flag set to determine port status.
Example:
nmap -sS -sV -sC -T4 -p 80,443 -oX scan_results.xml target.comThis command performs a SYN scan (-sS) on target.com, attempting to identify the services running on ports 80 and 443 (-sV), running script scans (-sC) for vulnerability checks and other information, using a fast timing template (-T4), and saving the results in XML format (-oX).
Output Formatting Flags: Controlling the Presentation
- -oA: Saves the scan results in all supported output formats, including normal text, XML, and Grepable.
- -oS: Outputs the results in a simple, human-readable format, suitable for quick analysis.
- -oE: Generates an output in a format suitable for importing into spreadsheet software.
- -d: Sets the debugging level, providing detailed information about the scan process and potential errors.
Example:
nmap -T4 -p 80,443 -oA scan_results target.comThis command scans target.com on ports 80 and 443, using a fast timing template (-T4), and saves the results in all supported output formats under the prefix "scan_results."
Advanced Flags: Expanding the Capabilities
- -Pn: Disables ping scanning, allowing for scanning of hosts that may not respond to ICMP requests.
- -D: Specifies a decoy list, sending probes from multiple IP addresses to obfuscate the scan origin.
- -f: Fragments the packets, potentially evading firewalls or intrusion detection systems.
- -g: Uses a specific gateway for the scan, allowing for control over the network path.
- -M: Performs a "masscan" scan, leveraging a distributed network of machines to accelerate the scanning process.
Example:
nmap -sS -T4 -p 80,443 -D 192.168.1.100,192.168.1.101 -f -oN scan_results.txt target.comThis command performs a SYN scan (-sS) on target.com, using a fast timing template (-T4), focusing on ports 80 and 443, using decoys from IP addresses 192.168.1.100 and 192.168.1.101 (-D), fragmenting the packets (-f), and saving the results to "scan_results.txt."
FAQs about Nmap Flags
1. What is the difference between -sT and -sS scans?
- -sT (TCP Connect Scan): Establishes a full TCP connection to the target port, sending SYN, ACK, and FIN packets. This is the most common and straightforward scan type but can be more intrusive and detectable.
- -sS (SYN Scan): Sends a SYN packet to the target port and analyzes the response to determine port status. This is a stealthier approach, as it does not fully establish a connection.
2. How do I scan a specific range of ports?
Use the -p flag followed by a comma-separated list of ports, or a range using a hyphen. For example, to scan ports 22, 80, and 443: nmap -p 22,80,443 target.com. To scan ports 1-1000: nmap -p 1-1000 target.com.
3. What is the purpose of the -T flag?
The -T flag sets the timing template, influencing the speed of the scan. Higher values (e.g., -T4) result in faster scans, while lower values (e.g., -T1) prioritize stealth and minimize network impact.
4. How can I save scan results in XML format?
Use the -oX flag followed by the desired filename. For example, to save the results to "scan_results.xml": nmap -oX scan_results.xml target.com.
5. What are some advanced techniques for evading detection?
- -f: Fragments packets to potentially bypass firewalls.
- -D: Specifies a decoy list, sending probes from multiple IP addresses to obfuscate the scan origin.
- -sI (Idle Scan): Leverages the network activity of other hosts to identify open ports without directly interacting with the target.
Tips for Effective Nmap Usage
- Start with basic scans: Begin with simple scans like -sT or -sS to get a general understanding of the target network.
- Use the -sV flag: Identify running services for more comprehensive analysis.
- Leverage scripts: Utilize Nmap’s script library for vulnerability checks, banner grabbing, and other advanced tasks.
- Experiment with timing templates: Adjust the -T flag to balance scan speed and stealth.
- Utilize output formatting options: Choose the most appropriate format for analysis and sharing.
Conclusion
Nmap flags are the key to unlocking the full potential of this powerful network exploration tool. By understanding the diverse range of flags and their implications, users can tailor their scans to specific needs, achieving comprehensive network analysis, security auditing, and vulnerability assessment. From basic target specification to advanced evasion techniques, Nmap’s flag system empowers users to explore and understand network environments with unparalleled depth and precision. Mastering the art of Nmap flags is an essential step for anyone seeking to navigate the complex landscape of modern networks.



Closure
Thus, we hope this article has provided valuable insights into Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags. We appreciate your attention to our article. See you in our next article!