Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags
Related Articles: Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags
Introduction
With great pleasure, we will explore the intriguing topic related to Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags

Nmap, the Network Mapper, is a powerful and versatile tool used for network discovery and security auditing. Its strength lies in its flexibility, which is achieved through a wide array of command-line flags. These flags allow users to customize Nmap’s behavior, tailoring scans to specific needs and objectives. This article provides a comprehensive guide to Nmap flags, exploring their functions, applications, and potential benefits.
Understanding the Basics: Nmap Flag Syntax
Nmap flags are typically preceded by a hyphen (-) or double hyphen (–), followed by the flag name. For instance, "-sT" or "–tcp-connect" both initiate a TCP connect scan. Flags can be combined in a single command, allowing for complex scan configurations.
Core Scanning Techniques: Unveiling the Network Landscape
Nmap’s core functionality revolves around scanning techniques, each designed for specific purposes. These techniques are defined by flags and offer different levels of detail and stealth.
- TCP Connect Scan (Flags: -sT, –tcp-connect): This is the default scan type, where Nmap attempts to establish a TCP connection with each target port. While straightforward, it is less stealthy and can be detected by intrusion detection systems.
- SYN Scan (Flags: -sS, –syn): This scan, also known as a half-open scan, sends a SYN packet (the first packet in a TCP handshake) to each target port. If the port is open, the target responds with a SYN-ACK packet. This technique is stealthier than a TCP connect scan as it avoids completing the TCP handshake.
- UDP Scan (Flags: -sU, –udp): Nmap sends UDP packets to each target port, checking for a response. This is particularly useful for identifying UDP-based services.
- FIN Scan (Flags: -sF, –fin): This scan sends a FIN packet to each target port. If the port is open, the target will respond with an RST (reset) packet. This scan is highly stealthy but can be less reliable than other options.
- Null Scan (Flags: -sN, –null): This scan sends a null packet to each target port. If the port is open, the target will respond with an RST packet. This scan is stealthy but may not be reliable with all systems.
- Xmas Scan (Flags: -sX, –xmas): This scan sends a packet with the FIN, PSH, and URG flags set. If the port is open, the target will respond with an RST packet. This scan is stealthy but can be less reliable than other options.
- Idle Scan (Flags: -sI, –idle): This scan leverages a zombie host to probe target ports, making it extremely stealthy. However, it requires a cooperating zombie host.
Beyond Scanning: Tailoring Your Nmap Experience
Nmap’s flexibility extends beyond basic scanning techniques. Flags offer control over various aspects of the scan, enabling customization for diverse scenarios.
Target Selection and Scope:
-
Host Specifying Flags:
- -R, –range: Defines the IP address range to scan.
- -sL, –list-scan: Scans a list of hosts provided in a file.
- -iL, –input-file: Reads a list of hosts from a file.
-
Port Specifying Flags:
- -p, –ports: Specifies the ports to scan. Can be individual ports (e.g., 80), port ranges (e.g., 1-1000), or common port lists (e.g., "top-1000").
- -F, –top-ports: Scans the top 1000 most common ports.
- -T, –top-ports-all: Scans the top 1000 most common ports for all protocols.
Output Formatting and Control:
- -oN, –normal-output: Saves scan results to a plain text file.
- -oX, –xml-output: Saves scan results in XML format.
- -oG, –grepable-output: Saves scan results in a format suitable for grepping.
- -v, –verbose: Increases output verbosity.
- -d, –debug: Enables debugging output.
- -q, –quiet: Reduces output verbosity.
Timing and Optimization:
- -T, –timing-template: Controls scan speed and timing.
- -r, –randomize-hosts: Randomizes the order in which hosts are scanned.
- -n, –no-dns: Disables reverse DNS lookups.
- -A, –all-ports: Scans all ports.
- -O, –osscan-guess: Attempts to identify the operating system of the target.
Advanced Techniques: Unlocking Deeper Insights
Nmap offers advanced features for in-depth network analysis and security assessments.
- Service and Version Detection (Flags: -sV, –version-intensity): Nmap probes services running on open ports, attempting to identify the service name and version.
- Operating System Detection (Flags: -O, –osscan-guess): Nmap analyzes network traffic patterns and responses to infer the operating system running on the target.
- Script Scanning (Flags: -sC, –script): Nmap can execute scripts against target hosts, performing various checks, including vulnerability detection, service enumeration, and credential testing.
- Exploitation (Flags: -e, –exploit): While not a primary function of Nmap, it can be used to execute exploits against discovered vulnerabilities.
FAQs by Nmap Flags
1. How can I scan a specific IP address range?
- Use the
-Ror--rangeflag followed by the IP address range (e.g.,nmap -R 192.168.1.1-10).
2. How can I scan only specific ports?
- Use the
-por--portsflag followed by the port numbers or ranges (e.g.,nmap -p 80,443 -R 192.168.1.1-10).
3. How can I save the scan results to a file?
- Use the
-oNor--normal-outputflag followed by the filename (e.g.,nmap -oN results.txt -R 192.168.1.1-10).
4. How can I identify the operating system of a target host?
- Use the
-Oor--osscan-guessflag (e.g.,nmap -O 192.168.1.1).
5. How can I run scripts against target hosts?
- Use the
-sCor--scriptflag (e.g.,nmap -sC 192.168.1.1).
Tips by Nmap Flags
-
Start with a basic scan: Use the default TCP connect scan (
-sT) to get an initial understanding of the network. -
Customize scan speed: Adjust the timing template (
-T) for faster or slower scans based on your needs. -
Use verbose output: Enable verbose output (
-v) for detailed information. - Save scan results: Save scan results to files for later analysis and documentation.
- Experiment with different scan techniques: Explore various scan techniques (SYN, UDP, FIN, etc.) to find the most suitable option for your specific scenario.
- Use scripts for advanced analysis: Leverage Nmap’s script engine to perform in-depth checks and gather valuable insights.
Conclusion by Nmap Flags
Nmap flags are essential for unlocking the full potential of this powerful network exploration tool. By understanding and utilizing these flags, users can tailor Nmap’s behavior to suit their specific needs, whether for basic network discovery, comprehensive security assessments, or advanced vulnerability analysis. The vast array of flags empowers users to customize their scans, optimize performance, and gain deeper insights into the network environment. Mastering Nmap flags is crucial for anyone involved in network administration, security auditing, or penetration testing.
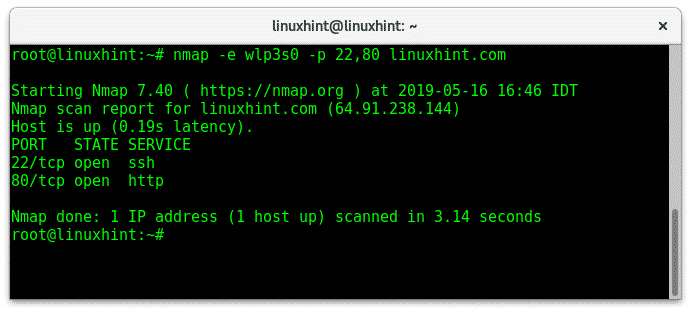

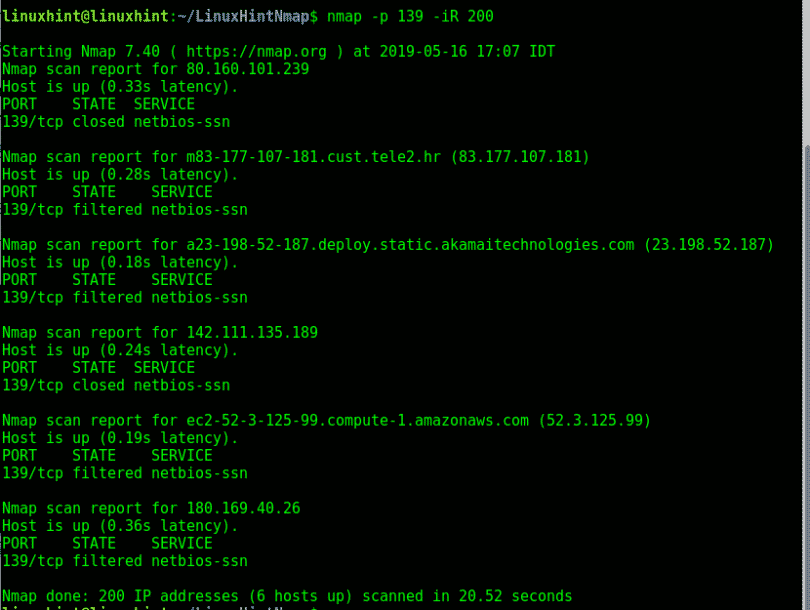

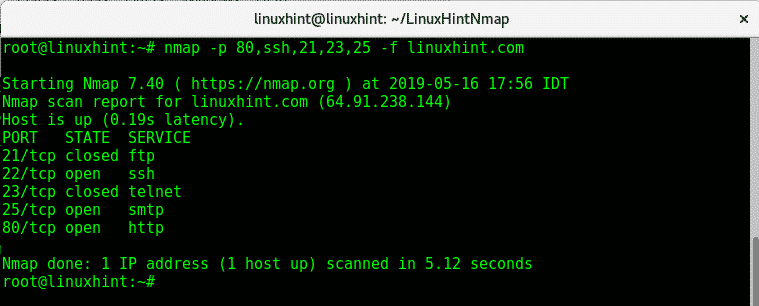
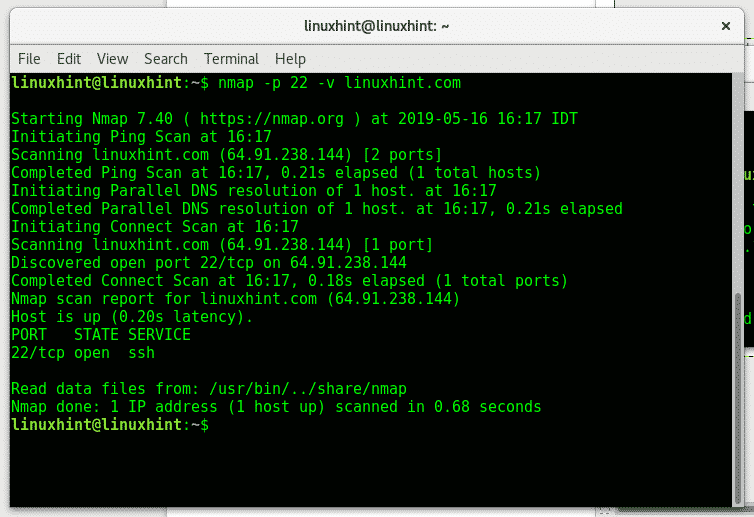

Closure
Thus, we hope this article has provided valuable insights into Unlocking the Power of Network Exploration: A Comprehensive Guide to Nmap Flags. We hope you find this article informative and beneficial. See you in our next article!