Unraveling the Power of Nmap: A Guide to Essential Commands
Related Articles: Unraveling the Power of Nmap: A Guide to Essential Commands
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unraveling the Power of Nmap: A Guide to Essential Commands. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unraveling the Power of Nmap: A Guide to Essential Commands
Nmap, the Network Mapper, stands as a cornerstone tool for network security professionals and enthusiasts alike. Its ability to scan networks and gather detailed information about devices, services, and vulnerabilities makes it indispensable for network administration, security auditing, and penetration testing. This comprehensive guide delves into the fundamental Nmap commands, empowering users to navigate the network landscape with precision and insight.
Understanding the Basics: A Foundation for Exploration
Nmap’s core functionality revolves around sending specially crafted packets to target hosts and analyzing the responses. This process, known as port scanning, provides valuable information about open ports, services running on those ports, and the operating system running on the host.
The simplest Nmap command is:
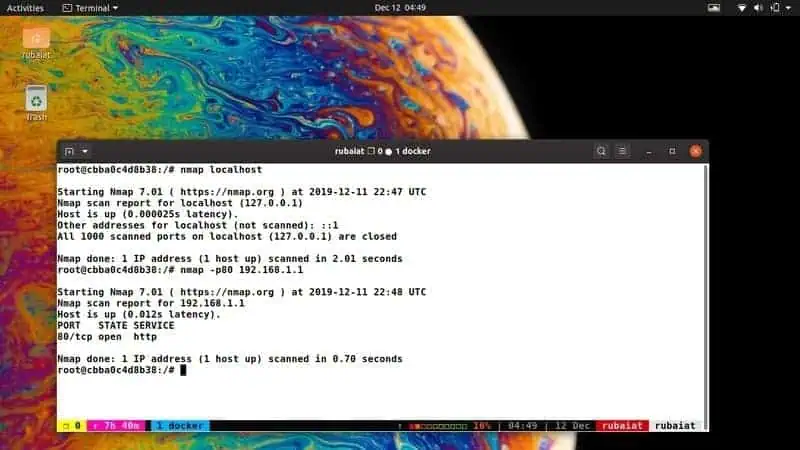
nmap <target>This command performs a basic scan, attempting to connect to all common ports on the target host. The target can be an IP address, hostname, or a range of IP addresses. For example, nmap 192.168.1.100 scans all common ports on the host with the IP address 192.168.1.100.
Beyond the Basics: Unveiling Nmap’s Capabilities
While a basic scan provides initial insights, Nmap offers a plethora of options to tailor scans for specific needs. Let’s explore some key commands that unlock Nmap’s full potential:
1. Port Scanning: Targeting Specific Ports
-
-p
: This option allows specifying a list of ports to scan. For instance,nmap -p 22,80,443 192.168.1.100scans ports 22, 80, and 443 on the target host. -
-p
: This option allows specifying a range of ports to scan. For example,nmap -p 1-1000 192.168.1.100scans ports 1 to 1000 on the target host. -
-T
: This option controls the scan speed. Nmap offers various timing templates like-T4for aggressive scanning,-T3for normal scanning, and-T1for stealth scanning.
2. Service Detection: Identifying Running Services
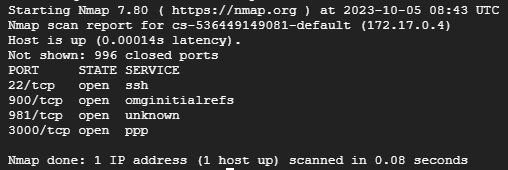
- -sV: This option enables service detection, identifying the specific services running on open ports. Nmap leverages a comprehensive database of service fingerprints to accurately identify applications like SSH, HTTP, and FTP.
- -A: This option combines service detection with operating system detection for a more detailed scan.
3. Operating System Detection: Unmasking the Target’s Identity
- -O: This option attempts to identify the operating system running on the target host. Nmap analyzes various network characteristics, such as TCP/IP stack behavior and response times, to infer the operating system.
- -sC: This option runs a set of default scripts that can further enhance operating system detection and identify specific vulnerabilities.
4. Network Scanning: Mapping the Network Landscape
- -T4: This option enables aggressive scanning, maximizing scan speed and reducing scan time.
- -F: This option performs a fast scan, focusing on common ports.
-
-iL
: This option allows reading a list of targets from a file. This is particularly useful for scanning large networks or lists of IP addresses.
5. Vulnerability Scanning: Identifying Potential Weaknesses
- -sC: This option runs a set of default scripts that can identify potential vulnerabilities.
- -sV: This option enables service detection, which can be used to identify specific versions of applications and their known vulnerabilities.
- –script
:<\/strong> This option allows running specific Nmap scripts to target known vulnerabilities or perform specialized scans.<\/li> <\/ul> FAQs: Addressing Common Queries<\/strong><\/p>
Q: What are the benefits of using Nmap?<\/strong><\/p>
A: Nmap offers numerous benefits, including:<\/p>
- Network Discovery:<\/strong> Identifying devices and services on a network.<\/li>
- Security Auditing:<\/strong> Assessing network security posture by identifying vulnerabilities.<\/li>
- Penetration Testing:<\/strong> Discovering potential attack vectors and vulnerabilities.<\/li>
- Network Management:<\/strong> Monitoring network health and troubleshooting issues.<\/li>
- Troubleshooting:<\/strong> Identifying network connectivity problems and resolving them.<\/li> <\/ul>
Q: How can I scan a specific port?<\/strong><\/p>
A: To scan a specific port, use the
-p<\/code> option followed by the port number. For example,nmap -p 80 192.168.1.100<\/code> scans port 80 on the target host.<\/p>Q: How can I scan a range of ports?<\/strong><\/p>
A: To scan a range of ports, use the
-p<\/code> option followed by a hyphen between the starting and ending port numbers. For example,nmap -p 1-1000 192.168.1.100<\/code> scans ports 1 to 1000 on the target host.<\/p>Q: How can I identify the operating system of a target host?<\/strong><\/p>
A: Use the
-O<\/code> option to attempt to identify the operating system running on the target host. Nmap analyzes various network characteristics to infer the operating system.<\/p>Q: How can I run a vulnerability scan?<\/strong><\/p>
A: Use the
-sC<\/code> option to run a set of default scripts that can identify potential vulnerabilities. Alternatively, use the--script<\/code> option to run specific Nmap scripts targeting known vulnerabilities.<\/p>Tips: Enhancing Nmap Usage<\/strong><\/p>
- Utilize Nmap’s script library:<\/strong> Nmap’s extensive script library offers specialized scans for identifying vulnerabilities, probing specific services, and gathering detailed information.<\/li>
- Experiment with timing templates:<\/strong> Nmap’s timing templates allow adjusting scan speed based on network conditions and target sensitivity.<\/li>
- Customize scan options:<\/strong> Tailor your scans to specific needs by combining various Nmap options.<\/li>
- Use output formats:<\/strong> Nmap supports various output formats like XML, greppable, and normal, allowing you to tailor results for analysis and reporting.<\/li>
- Explore Nmap’s documentation:<\/strong> Nmap’s comprehensive documentation provides detailed information about all commands, options, and scripts.<\/li> <\/ul>
Conclusion: Embracing the Power of Nmap<\/strong><\/p>
Nmap’s versatile command-line interface and extensive feature set empower users to gain valuable insights into network infrastructure. By mastering the fundamental commands and exploring Nmap’s advanced capabilities, individuals can effectively conduct network scans, identify vulnerabilities, and enhance network security. Nmap remains an indispensable tool for network professionals and security enthusiasts, enabling them to navigate the complex world of networks with precision and confidence. <\/p>





 <\/p>
<\/p>
Closure<\/h2>
Thus, we hope this article has provided valuable insights into Unraveling the Power of Nmap: A Guide to Essential Commands. We hope you find this article informative and beneficial. See you in our next article!<\/p>
- Experiment with timing templates:<\/strong> Nmap’s timing templates allow adjusting scan speed based on network conditions and target sensitivity.<\/li>
- Security Auditing:<\/strong> Assessing network security posture by identifying vulnerabilities.<\/li>
- Network Discovery:<\/strong> Identifying devices and services on a network.<\/li>