Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Stealth Scan
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Stealth Scan
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Stealth Scan. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Stealth Scan
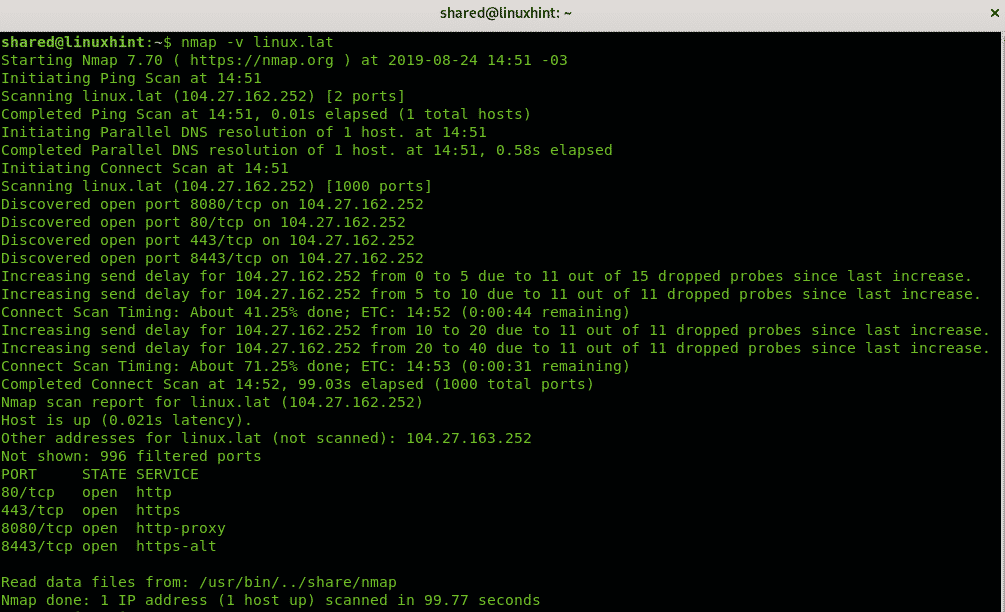
Nmap, the ubiquitous network scanner, provides a plethora of options for exploring and understanding network landscapes. Among its arsenal of flags, the -sc flag stands out as a powerful tool for conducting stealthy scans, minimizing the chances of detection while gathering valuable information. This comprehensive guide will delve into the intricacies of this flag, elucidating its functionality, applications, and significance in the realm of network security assessments.
Understanding the Essence of Stealth Scans
Network security assessments often necessitate the ability to gather information without raising alarms. Traditional Nmap scans, while effective, can trigger intrusion detection systems (IDS) and firewalls, potentially leading to unwanted scrutiny or even blocking access. The -sc flag, often referred to as the "stealth scan," addresses this challenge by employing techniques that minimize the scan’s footprint, making it less likely to be detected.
The Mechanics of Stealthy Scanning
The -sc flag instructs Nmap to perform a stealth scan by utilizing a combination of strategies:
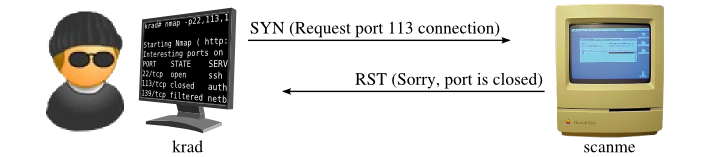
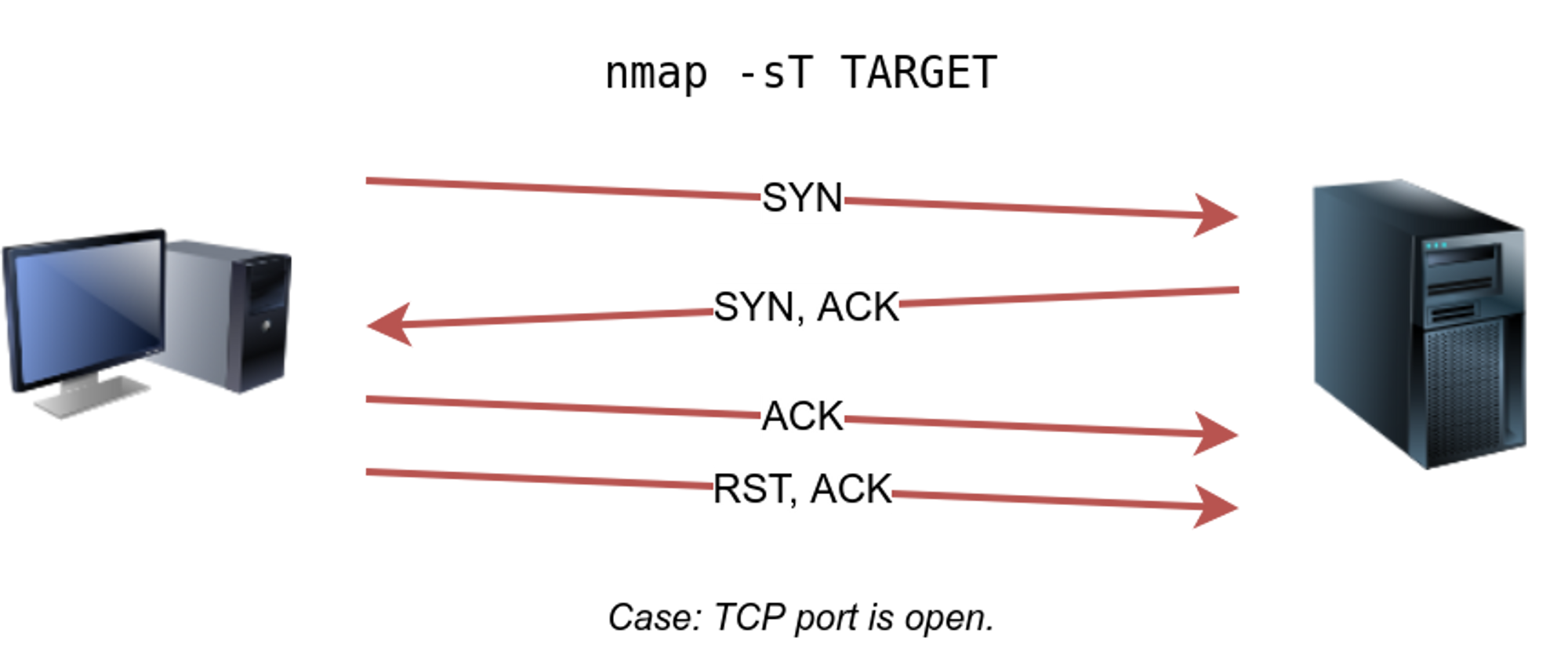
- TCP SYN Scan with Minimal Packet Transmission: Instead of sending the full TCP handshake, Nmap sends only the initial SYN packet, the first step in the TCP connection establishment process. This minimizes the number of packets transmitted, making the scan less conspicuous.
- Port Scanning with Minimal Packet Transmission: Nmap employs techniques like the "null scan" and "fin scan" that rely on sending minimal packets to probe target ports. These techniques exploit vulnerabilities in TCP implementations to determine port status without triggering full connections.
- Timing and Packet Sequencing: Nmap carefully adjusts the timing and sequencing of packets to further reduce the scan’s visibility. By sending packets at specific intervals and manipulating their order, Nmap can blend in with legitimate network traffic, making it harder for intrusion detection systems to distinguish malicious activity.
Benefits of Utilizing Stealth Scans
The ability to conduct stealthy scans offers numerous benefits for network security professionals and enthusiasts alike:
- Reduced Detection Risk: By minimizing the scan’s footprint, the -sc flag significantly reduces the likelihood of triggering intrusion detection systems and firewalls, allowing for more discreet information gathering.
- Enhanced Security Assessments: Stealth scans enable security professionals to conduct thorough vulnerability assessments without alerting potential attackers or compromising the security posture of the target network.
- Improved Reconnaissance: In penetration testing scenarios, stealth scans allow attackers to gather information about a target network without alerting defenders, providing valuable insights for crafting effective attacks.
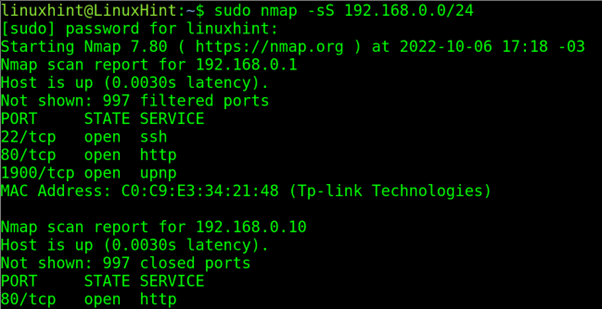
- Network Auditing: System administrators can leverage stealth scans to audit network configurations and identify potential security vulnerabilities without disrupting normal operations.
- Compliance and Legal Considerations: Stealth scans can be valuable in situations where traditional scans are prohibited due to legal or compliance requirements, ensuring that network assessments are conducted ethically and responsibly.
Applications of Stealth Scans
The -sc flag finds diverse applications across various network security domains:
- Vulnerability Assessment: Security professionals utilize stealth scans to identify potential vulnerabilities in networks and systems, providing critical information for mitigating risks and improving security posture.
- Penetration Testing: Ethical hackers employ stealth scans during penetration testing engagements to gather information about target networks, identify potential attack vectors, and assess the effectiveness of security controls.
- Network Monitoring and Auditing: System administrators use stealth scans to monitor network activity, identify unauthorized devices, and ensure compliance with security policies.
- Incident Response: In the event of a security breach, stealth scans can be used to identify the extent of the compromise, gather evidence, and assist in remediation efforts.
- Research and Development: Researchers and security enthusiasts utilize stealth scans to study network behavior, explore new vulnerabilities, and develop innovative security tools and techniques.
FAQs: Demystifying Stealth Scans
1. What are the limitations of stealth scans?
While stealth scans offer significant advantages, they are not foolproof. Advanced intrusion detection systems and firewalls can still detect stealthy scans, especially if they are configured to look for specific patterns of network traffic. Additionally, stealth scans may not be effective against sophisticated security measures like deep packet inspection (DPI), which can analyze the content of network packets.
2. Is it ethical to use stealth scans?
The ethical implications of using stealth scans depend on the context and intent. It is generally considered ethical to use stealth scans for legitimate security assessments and penetration testing with explicit permission from the target organization. However, using stealth scans for malicious purposes, such as unauthorized network access or data theft, is unethical and illegal.
3. Can stealth scans be used to bypass firewalls?
Stealth scans can help minimize the chances of detection by firewalls, but they cannot guarantee bypass. Firewalls can be configured to block specific types of traffic, including stealth scans, and advanced firewalls may employ techniques like deep packet inspection to detect and block malicious activity.
4. How can I configure Nmap for stealth scans?
The -sc flag is the primary command for initiating stealth scans in Nmap. However, additional flags can be used to customize the scan behavior. For example, the -T4 flag can be used to adjust the scan timing, while the -F flag can be used to limit the number of ports scanned.
5. What are some alternatives to stealth scans?
While stealth scans offer a valuable approach to network security assessments, alternative techniques exist for gathering information about networks and systems. These include:
- Active Scans: Traditional Nmap scans that send full TCP handshakes, providing more detailed information but potentially triggering alarms.
- Passive Scans: Techniques that rely on analyzing existing network traffic, offering a non-intrusive approach but providing less comprehensive information.
- Port Knocking: A technique that uses specific port sequences to establish communication with a target system, offering a stealthy alternative to traditional port scanning.
Tips for Effective Stealth Scanning
- Understand the Target Network: Before conducting a stealth scan, it is crucial to understand the target network’s security posture, including the types of firewalls, intrusion detection systems, and security measures in place.
- Customize Scan Parameters: Adjust the scan timing, port range, and other parameters to optimize the scan for stealth and minimize the risk of detection.
- Use a VPN or Proxy: Consider using a VPN or proxy to mask your IP address and further reduce the chances of detection.
- Monitor for Alerts: Keep an eye on any alerts or logs generated by the target network during the scan to identify potential issues or detection events.
- Respect Legal and Ethical Boundaries: Always conduct stealth scans responsibly, adhering to legal and ethical guidelines, and obtaining permission from the target organization when necessary.
Conclusion: The Power of Stealth in Network Security
The -sc flag in Nmap empowers network security professionals and enthusiasts with the ability to conduct stealthy scans, minimizing the risk of detection while gathering valuable information. By leveraging the techniques of minimized packet transmission, timing adjustments, and strategic port probing, stealth scans offer a discreet approach to network security assessments, penetration testing, and network monitoring. Understanding the nuances of stealth scans and their applications is crucial for navigating the complex landscape of network security, enabling responsible and effective information gathering without compromising the integrity of target networks.




Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Stealth Scan. We appreciate your attention to our article. See you in our next article!