Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Thorough Scans
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Thorough Scans
Introduction
With great pleasure, we will explore the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Thorough Scans. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Thorough Scans
Network security professionals and penetration testers rely on a diverse range of tools to assess network vulnerabilities and gain insights into network infrastructure. Among these, Nmap, the Network Mapper, stands out as a powerful and versatile tool. Nmap’s comprehensive scanning capabilities provide a detailed picture of network devices, services, and potential security weaknesses. This article delves into the intricacies of Nmap’s thorough scans, exploring their application, benefits, and limitations, while addressing common questions and offering practical tips for effective utilization.
The Essence of Thorough Network Exploration
Nmap’s thorough scans, often referred to as "intense" or "aggressive" scans, are designed to uncover as much information as possible about a target network. Unlike basic scans that focus on identifying open ports, thorough scans employ a combination of techniques to paint a comprehensive portrait of the network landscape. These techniques include:
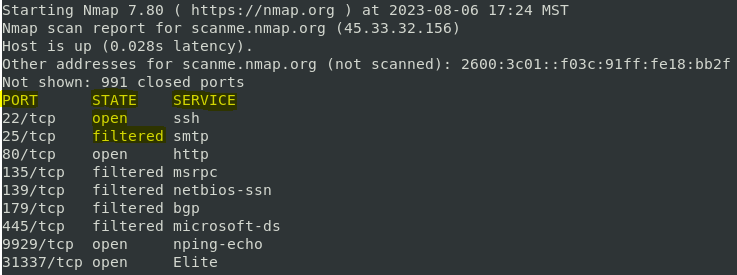
- Port Scanning: This fundamental aspect of Nmap’s operation involves probing specific ports on target devices to determine which ports are open and potentially host services.
- Service Version Detection: Nmap goes beyond simply identifying open ports; it attempts to determine the specific service running on each port. This identification is achieved by analyzing the responses from the target device, often by sending specially crafted packets to elicit characteristic responses from the service.
- Operating System Detection: Nmap utilizes a sophisticated technique known as "fingerprint analysis" to identify the operating system running on target devices. This involves analyzing the timing of responses, the specific data packets exchanged, and other network characteristics to deduce the underlying operating system.
- Script Scanning: Nmap integrates a vast library of scripts that can automate various tasks, including vulnerability detection, service discovery, and network analysis. These scripts can be customized and extended to cater to specific security assessment needs.
Understanding the Benefits of Thorough Scans
The thoroughness of Nmap scans offers numerous benefits for network security professionals, penetration testers, and system administrators:
- Detailed Network Visibility: Thorough scans provide a comprehensive understanding of the network infrastructure, including the types of devices present, the services they offer, and the operating systems they run. This detailed information is essential for informed decision-making regarding network security and management.
- Vulnerability Identification: By uncovering the specific services and versions running on network devices, thorough scans enable the identification of known vulnerabilities. This information allows security professionals to prioritize remediation efforts and mitigate potential security risks.
- Network Mapping: Nmap’s thorough scans can generate detailed network maps, visually representing the interconnectedness of devices and services. This visualization aids in understanding network topology, identifying potential security bottlenecks, and streamlining troubleshooting efforts.
- Security Posture Assessment: By combining port scanning, service version detection, and operating system identification, thorough scans provide a holistic picture of the network’s security posture. This assessment allows organizations to identify weaknesses and implement appropriate security measures.
- Incident Response: In the event of a security incident, thorough scans can assist in identifying compromised devices, tracing the attack path, and mitigating further damage. The comprehensive information gathered can expedite incident response efforts and minimize the impact of security breaches.
Considerations and Limitations of Thorough Scans
While thorough scans offer valuable insights, they also come with certain considerations and limitations:
- Network Impact: Extensive scanning can consume significant network bandwidth and resources, potentially impacting the performance of other network services and applications. This is particularly relevant in large networks or environments with limited bandwidth.
- Detection by Intrusion Detection Systems (IDS): Nmap’s aggressive scanning techniques can trigger alarms on intrusion detection systems, potentially leading to false positives and security alerts. It is crucial to coordinate with network security teams and inform them about planned Nmap scans to avoid unnecessary disruptions.
- Legal and Ethical Considerations: Depending on the target network and the specific scanning techniques employed, thorough Nmap scans may raise legal and ethical concerns. It is essential to adhere to local laws and regulations regarding network scanning and ensure that scans are conducted with proper authorization and consent.
Frequently Asked Questions (FAQs) about Nmap Thorough Scans
Q: What is the difference between a basic scan and a thorough scan in Nmap?
A: A basic scan focuses on identifying open ports on target devices, while a thorough scan goes beyond this by attempting to identify the specific services running on each port, the operating system of the device, and even potential vulnerabilities.
Q: Are thorough Nmap scans always necessary?
A: The necessity of a thorough scan depends on the specific objectives of the security assessment. In some cases, a basic scan may suffice, while in other cases, a more comprehensive approach is required for a thorough understanding of the network’s security posture.
Q: How can I reduce the impact of Nmap scans on network performance?
A: To minimize the impact, consider scheduling scans during off-peak hours, limiting the scan scope to specific devices or subnets, and using techniques like scan rate limiting to control the number of probes sent per second.
Q: Are there any legal or ethical considerations for conducting thorough Nmap scans?
A: It is crucial to comply with local laws and regulations regarding network scanning. Always obtain proper authorization and consent before scanning networks that are not under your direct control.
Tips for Effective Nmap Thorough Scans
- Define Scan Scope: Clearly define the target devices, subnets, or ranges of IP addresses to be scanned. This helps focus the scan and minimize unnecessary network traffic.
- Utilize Scan Rate Limiting: Control the number of probes sent per second to avoid overwhelming target devices and minimize network impact.
- Employ Scripting: Leverage Nmap’s scripting capabilities to automate repetitive tasks, customize scans, and enhance the efficiency of the assessment process.
- Analyze and Interpret Results: Thoroughly analyze the scan results, paying attention to open ports, service versions, operating systems, and potential vulnerabilities.
- Document Findings: Document the scan results, including the methodology used, the identified vulnerabilities, and any remediation actions taken.
Conclusion
Nmap’s thorough scans provide a powerful tool for network security professionals, penetration testers, and system administrators seeking comprehensive insights into network infrastructure. By combining port scanning, service version detection, operating system identification, and script scanning, these scans deliver detailed network visibility, vulnerability identification, and a holistic picture of the network’s security posture. While thorough scans can be resource-intensive, their benefits in terms of security awareness and vulnerability mitigation far outweigh the potential drawbacks. By carefully planning, executing, and interpreting thorough Nmap scans, organizations can enhance their network security posture and proactively address potential vulnerabilities before they are exploited.




Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap’s Thorough Scans. We hope you find this article informative and beneficial. See you in our next article!
