Unveiling the Power of Nmap’s Stealthy Scan: A Comprehensive Exploration of the -pn Flag
Related Articles: Unveiling the Power of Nmap’s Stealthy Scan: A Comprehensive Exploration of the -pn Flag
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Power of Nmap’s Stealthy Scan: A Comprehensive Exploration of the -pn Flag. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Power of Nmap’s Stealthy Scan: A Comprehensive Exploration of the -pn Flag
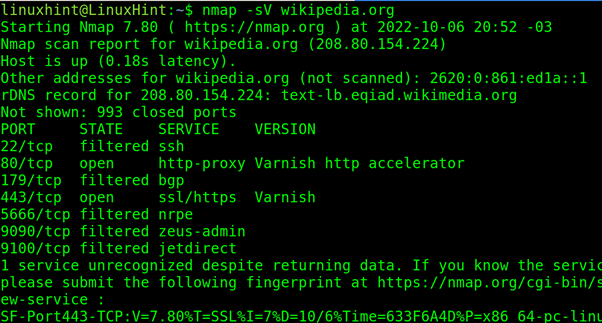
Nmap, the Network Mapper, is a cornerstone tool for network administrators and security professionals, offering a versatile toolkit for probing and understanding network infrastructure. Within its extensive arsenal of flags, the -pn flag stands out as a potent tool for conducting stealthy scans, prioritizing discretion and minimizing the risk of detection. This article delves into the intricacies of the -pn flag, exploring its functionality, applications, and the benefits it offers in various scenarios.
Understanding the -pn Flag: A Stealthy Approach
The -pn flag instructs Nmap to perform a scan without sending any packets that would reveal the source port of the scan. This is achieved by employing a technique known as "IP ID Spoofing," where Nmap strategically manipulates the identification field (IP ID) of the packets it sends. By sending packets with seemingly random IP IDs, Nmap effectively masks its source port, making it appear as if the scan originated from a different host.
The Mechanics of Stealth: IP ID Spoofing in Action
IP ID spoofing is a complex technique that relies on the inherent behavior of network devices. When a packet traverses a network, it is assigned a unique IP ID by the originating device. This ID acts as a tracking mechanism, allowing routers and firewalls to identify and manage the flow of packets. Nmap exploits this mechanism by manipulating the IP ID field, effectively creating a false origin for the scan packets.
The -pn flag, when used in conjunction with other Nmap scan types, enables a range of stealthy scanning techniques:
- Ping Scan ( -sP ): This scan type uses ICMP echo requests (pings) to determine if a host is alive. When combined with -pn, the ICMP packets are sent with spoofed IP IDs, masking the source port and reducing the likelihood of detection.
- TCP Connect Scan ( -sT ): This scan type attempts to establish a TCP connection with the target port. The -pn flag enhances stealth by spoofing the IP ID of the SYN packets, making it difficult for firewalls or intrusion detection systems (IDS) to identify the scan.
- UDP Scan ( -sU ): Similar to the TCP Connect Scan, the UDP scan sends UDP packets to the target port. The -pn flag effectively disguises the scan by spoofing the IP ID of the UDP packets.
The Advantages of a Stealthy Approach: Why -pn Matters
The -pn flag offers several distinct advantages in network scanning:
- Reduced Detection: The primary benefit of using -pn is its ability to minimize the risk of detection by firewalls, intrusion detection systems, and other security mechanisms. By masking the source port, Nmap’s scans become less conspicuous, making it harder for security systems to identify and block them.
- Increased Discretion: In scenarios where stealth is paramount, such as penetration testing or reconnaissance, -pn allows for discreet network exploration. This prevents unwanted alerts and minimizes the risk of triggering security responses.
- Enhanced Flexibility: The -pn flag can be combined with other Nmap scan types, offering a wide range of options for tailored scans. This flexibility allows for a more nuanced approach to network analysis, enabling security professionals to gather specific information without compromising stealth.
- Minimizing Network Impact: By minimizing the number of packets sent and avoiding the use of well-known ports, the -pn flag reduces the potential impact on network performance. This is especially valuable in environments where network bandwidth is limited or where excessive network activity could trigger alerts.
Understanding the Limitations: When -pn Might Not Be Ideal
While the -pn flag offers significant advantages, it’s important to understand its limitations:
- Limited Information Gathering: The use of -pn can hinder the ability to gather certain types of information. For example, some scan types rely on specific port behaviors to identify services, which may be obscured by IP ID spoofing.
- Potential for False Positives: IP ID spoofing can sometimes lead to false positives, where a host appears to be alive even if it is not. This can occur when the spoofed packets reach the destination but are not acknowledged by the target host.
- Not a Guarantee of Invisibility: While -pn significantly reduces the likelihood of detection, it does not guarantee complete invisibility. Advanced security systems may still be able to identify and block spoofed packets.
- Ethical Considerations: It is crucial to use the -pn flag responsibly and ethically. Always obtain explicit permission before conducting scans on networks you do not own or manage.
FAQs about the -pn Flag
Q: Can I use the -pn flag with all Nmap scan types?
A: While -pn can be used with most Nmap scan types, its effectiveness may vary depending on the specific scan technique. Some scan types, such as the SYN scan ( -sS ), rely on specific port behaviors that can be obscured by IP ID spoofing.
Q: Is using -pn always the best option?
A: No, the -pn flag is not always the best choice. In some scenarios, a more traditional scan might be more effective or necessary. Factors to consider include the specific information being sought, the target network’s security posture, and the potential impact of the scan.
Q: Can I use -pn to bypass firewalls?
A: The -pn flag does not bypass firewalls. Firewalls may still block packets based on other criteria, such as the source IP address or the target port. However, -pn can make it more difficult for firewalls to identify and block the scan.
Q: What are the ethical implications of using -pn?
A: As with any network scanning tool, it is essential to use the -pn flag ethically and responsibly. Always obtain explicit permission before scanning networks you do not own or manage. Avoid scanning networks without a legitimate purpose, and respect the privacy and security of others.
Tips for Using the -pn Flag Effectively
- Combine -pn with other flags: The -pn flag can be used in conjunction with other Nmap flags to create customized scans. For example, combining -pn with -sS (SYN scan) can create a stealthy scan that is less likely to trigger alerts.
- Test your scans: Before conducting a full scan, test the -pn flag on a small subset of the target network to ensure it is working as intended and to assess the potential impact on network performance.
- Be aware of the limitations: Remember that -pn does not guarantee complete invisibility. Advanced security systems may still be able to detect and block spoofed packets.
Conclusion: Embracing Stealth in Network Analysis
The -pn flag empowers Nmap users with the ability to conduct stealthy scans, minimizing the risk of detection and enhancing discretion. By leveraging IP ID spoofing, -pn allows for discreet network exploration, offering a valuable tool for penetration testing, reconnaissance, and network analysis. However, it is crucial to use this flag responsibly, understanding its limitations and adhering to ethical considerations. By embracing the power of stealth, network administrators and security professionals can gain a deeper understanding of network infrastructure while minimizing the potential impact on security and performance.
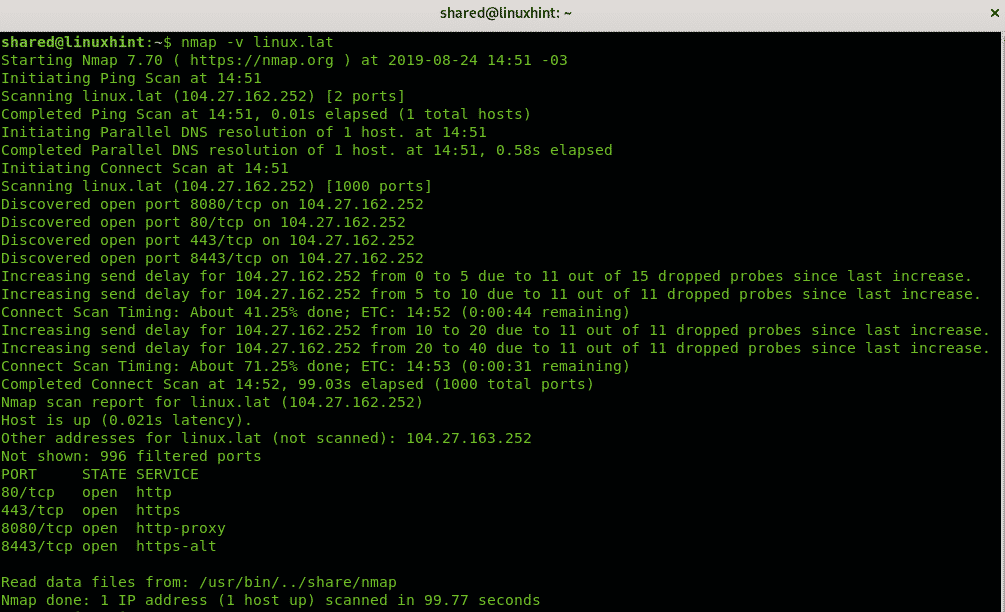

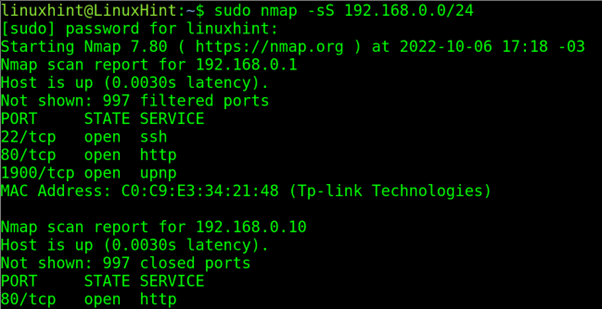
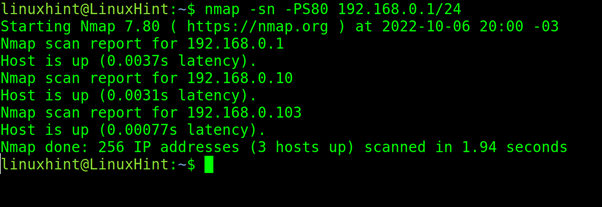

Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Nmap’s Stealthy Scan: A Comprehensive Exploration of the -pn Flag. We thank you for taking the time to read this article. See you in our next article!